Computer Homeostasis
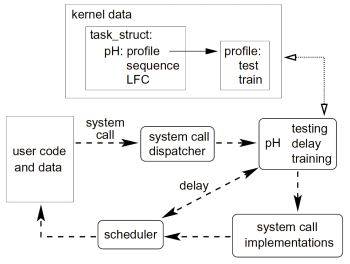
The next generation of computer-security programs put a new twist on the concept of virus protection. They use defensive techniques borrowed straight from the human immune system to control electronic invaders. Most of the anti-virus programs on computers today are designed to take drastic counter-measures against bugs. But the cure can be worse than the disease. An aggressive reaction can drain system resources and cripple short-term performance, which is a problem particularly for big networks of interconnected machines.
When we get sick, our immune systems take a different approach. Rather than slash-and-burn, they work to contain the virus, then gradually bring our systems back to equilibrium. The idea that this contain-and-control approach, which biologists call homeostasis, could furnish a better model for computer security was born at a 1998 IMA conference which included computer scientists and immunologists. The idea evolved into the Ph.D. thesis of participant Anil Somayaji and then into software for the open-source Linux operating system. Now it's reaching the mainstream. Hewlett-Packard and other major companies are rolling out new security products built around the concepts generated at the IMA conference.