Interfaces
Essays and Reviews in Computing and Culture

Interfaces publishes short essay articles and essay reviews connecting the history of computing/IT studies with contemporary social, cultural, political, economic, or environmental issues. It seeks to be an interface between disciplines, and between academics and broader audiences.
Co-Editors-in-Chief: Jeffrey R. Yost and Amanda Wick
Managing Editor: Melissa J. Dargay

After overseeing the Charles Babbage Institute's Oral History Program for 26 years, initially as Associate Director and now as CBI Director, and publishing Making IT Work: A History of the Computer Services Industry (MIT Press), which discusses the remarkable growth of this sector in India, I was thrilled to attend Harvard Business School's (HBS) conference, "Oral History and Business in the Global South." This reviews the event and the ongoing “Creating Emerging Markets” Oral History Project, which has been running for twelve years. The project is led by two HBS professors: leading business historian Goeffrey Jones (who holds the Isidor Straus Chair in Business History, the same endowed chair Alfred Chandler long held) and standout scholar of Entrepreneurship and Strategy Tarun Khanna (who holds the Jorge Paulo Lemann Professorship). I also reflect on “Creating Emerging Markets” in terms of methodology, products, and uses relative to other oral history programs including CBI’s.
The design of Jones’ and Khanna’s conference was tremendous, much like the leadership of their oral history project. HBS Research Associate Maxim Pike Harrell provides skilled coordination to the project, and he saw to every detail to make the event run flawlessly. At the end of the essay, I also briefly discuss the remarkable Baker Library, of which, attendees received a wonderful behind-the-scenes tour from Senior Director of Special Collections Laura Linard.
The HBS event and HBS oral history project connect to computing and the digital world in many ways. These points of connections include both producers and users of digital technology in business in the Global South. Additionally, HBS is developing enhancements to generative artificial intelligence tools to better facilitate the use of their oral history resources. While I highlight these as a part of this Interfaces essay, my discussion is not limited to the digital realm.
The quality of every paper at this conference was excellent. While I mention them all below, I discuss a handful in a bit more detail. This is merely to offer a greater sense of the event and to add depth to the review. The conference was organized around themes of oral history methods, research uses, teaching uses, gender, and Global South geographies (Africa, Latin America, and India).
From Bollywood to Augmented Retrieval with Generative AI
The conference kicked off with a panel on “New Approaches to Building and Using Oral Histories,” which was expertly framed by convener Susie Pak, a Professor of History at St. John’s University. The opening speaker was Sudev Sheth, a historian and international studies faculty member of the Lauder Institute at Wharton School of Management, University of Pennsylvania. This was the perfect start to this event, as it offered a rich framing of oral history relative to other potential, but sometimes absent or unavailable resources such as archival collections. As such, Sheth spoke of oral history as “Unconventional Sources,” drawing from his collaborative research on the history of race and gender in Bollywood, India’s film industry. Bollywood, with fewer capital resources, produces far more films annually than Hollywood and has for decades.
For many industries, topics, and themes in business history globally, archival records either were not retained, processed, and preserved, or are not accessible to academic and other researchers, for instance, closed corporate collections. The lack of available archives is even more pronounced in the Global South where resources for archival preservation are often scarce. Sheth’s insightful talk demonstrated how oral history was essential to studying, enlivening, and giving voice to marginalized historical actors. He did this with a case study on race and gender discrimination in Bollywood. Sheth demonstrated how Bollywood, for decades has privileged lighter-skinned actors on screen, as well as presented women in submissive and stereotypical ways, and lacking in agency. He highlighted a disturbing tendency in Bollywood to have long scenes of men dominating women, including gratuitous rape scenes. Sheth then presented video oral history snippets of Bollywood women actors who explained how they condemned and strongly resisted this practice.

This recovery of otherwise lost voices rang true to me, and it is exactly why at the Babbage Institute we have aimed at doing more interviews with women programmers, systems analysts, entrepreneurs, and computer users over the past two decades. This includes a project past CBI Director Thomas Misa did for the Sloan Foundation on women programmers and one I did on women entrepreneurs in software and services. Similarly, to HBS “Creating Emerging Markets,” we often use these oral histories, along with available archival and other research, in our publications. More importantly, these oral histories become resources for others, especially academics and graduate students, to use. As both a research institute and the leading archive for the history of the digital world, CBI oral histories open up rich archival collection development opportunities.
A difference between CBI relative to “Creating Emerging Markets” is we use video or audio recordings only to create transcripts that are edited for accuracy by interviewees and interviewers. This extends from our research infrastructure mission. It might reduce the educational use of the interviews (though there are some, as we see syllabi online assigning them and daily spikes in usage). “Creating Emerging Markets,” likewise, produces edited transcripts for research, but also creates professional video and snippets. This enables HBS’ collection to facilitate tremendous educational opportunities, which fits HBS so well, a school that sets the standard and influences business and management education throughout the world like no other. HBS does this through its exceptional faculty and its unparalleled (both in size and quality) 50,000 HBS-published case studies.
For those interested in this work on the history of Bollywood I would highly recommend Sudev Sheth, Geoffrey Jones, and Morgan Spencer’s compelling article, “Emboldening and Contesting Gender and Skin Color Stereotypes in the Film Industry in India, 1947-1991.” This was published in the Autumn 2021 (95:3) issue of Harvard Business Review.
The second paper of the opening session, while quite different, was equally engaging and spoke to issues of preservation. Vice President for Communication of Sweden’s Centre for Business History Anders Sjöman spoke on the model of his nonprofit organization. The Centre for Business History (CBH) is a large nonprofit with a wholly owned subsidiary services company. It provides archival storage, processing, editorial, historical analysis, writing/publishing, and related services to companies in Sweden. The CBH has hundreds of clients, and they include globally recognized names such as IKEA and Ericsson. The nonprofit is owned by its members, and the companies it works with to meet their history and archives needs. At 85,000 linear meters of documents, photographs, film, and video, it is one of the largest business archives in the world.
In the 1990s, as a doctoral student in history specializing in business, labor, and technology, I was introduced to and found organizational history and consulting fascinating. At the time, I worked as a researcher/historian for The Winthrop Group, a prominent US-based business history and archives consultancy located in Cambridge, Massachusetts. For three years I helped to research and assist with writing a major Harvard Business School Press book on the Timken Company (Pruitt w/ Yost, 1998). Since then, in addition to my faculty and center director post, I have continued to do a bit of historical consulting for business and nonprofit organizations. I like the idea of a nonprofit providing archival and historical preservation and analysis services, where the companies using the services are members and co-owners. This is a model that could work well for other countries and regions of the world.
The final paper of the opening session was by HBS’ Director of Architecture and Data Platforms Brent Benson and Maxim Harrell. They discussed using augmented retrieval generation—setting limits and parameters to HBS’ “Creating Emerging Markets” resources/data—as tools to better facilitate the usage of the collections and content generation. While, generally, I am extremely skeptical and critical of generative AI (as it generates based on data without understanding the data’s contexts) and believe it introduces a host of social bias-amplifying risks and realities, I found this discussion of augmented retrieval generation interesting. I was impressed that in the presentation, and their responses to questions, the presenters acknowledged risks and were carefully considering them in developing and refining these tools to augment search and use of “Creating Emerging Markets” oral history data. Regardless, this engaging work sparked rich discussion concerning new automation tools versus or in conjunction with traditional metadata of descriptors, abstracts, and finding aids, along with Boolean search.
Oral History as a Research Tool
The second session was on “Employing Oral History in Research.” It began with Lansberg Gersick Advisors (LGA) and Harvard adjunct Devin Deciantis’ discussion of the continuity of family enterprises in high-risk environments, focusing on his work and research in Venezuela. Oral history, documentation, and learning from the past can be helpful to meeting the challenges of generational transition of family businesses. In risky environments such as that of Venezuela with its soaring homicide rate, this can be all the more daunting, and all the more important given resources are scarcer. Deciantis is a particularly gifted and thoughtful orator, and this was an incredible talk. University of Texas A&M San Antonio historian Zhaojin Zeng next gave an impressive paper on the politics of doing archival research and oral history in China, indicating there are both significant possibilities and challenges. People openly dissenting on record from the Chinese Government’s standard or preferred perspective on issues and history can face risks. Finally, Meg Rithmire, a political scientist at HBS, sparked a discussion on the differences between interviews in social science versus oral history. This includes terminology and practice with gathering, saving, processing/editing, and making interview data publicly available.
Oral History of Gender and Business in the Global South
With my strong interest in social history, and especially gender history and gender studies in business, I found the three papers on “Gender Dynamics through Oral Histories in Business” especially intriguing. The oral histories for the “Creating Emerging Market” Project have generally been conducted in-person—interviewer, interviewee, and a film crew (though experimentation with enhanced video conferencing tools is also underway with the project).
The scholar who has done more in-person oral histories for the project than anyone in the Global South, Andrea Lluch, gave two brilliant talks in different sessions of the event. Lluch holds professorships at the School of Management, University of Los Andes, Columbia, and at the National University of La Pampa in Argentina. Additionally, she is a Researcher at the National Council of Scientific and Technical Research of Argentina. Her research and oral histories focusing on women entrepreneurs span both Argentina and Columbia. Among the various lessons, she emphasized are the importance and learning possibilities from interviewing throughout the hierarchies of organizations, providing an example of drug cartels.
Rounding out this session were outstanding papers by standout business historians Paula de la Cruz-Fernández (University of Florida) and Gabriela Recio (Business History Group, Mexico City). Fernández’s talk focused on capturing circumstance and historical contingency in exploring one woman entrepreneur in Miami, Florida, in “Estoy, in Right Place,” while Recio explored several women leaders’ experiences as they tried to navigate the male-dominated business culture.
In a different setting, but with the same principle of navigating organizational hierarchies and gaining understanding, just over a decade ago, I had the opportunity to do a sponsored research project with Thomas Misa. This project examined the impact of National Science Foundation Cyberinfrastructure (FastLane & internal e-Jacket) on the scientific and engineering research community it serves, as well as NSF as an organization. It was an oral history-based research project as few documents existed. We conducted in-person oral histories with four hundred people at 29 universities (vice presidents for research, deans, PIs, sponsored research administrators, and department administrators) and at NSF (top leadership, division directors, program officers, administrative assistants, and clerical staff). Our understanding of universities, NSF, and social (race and gender) and research impacts were so thoroughly enhanced by getting the perspectives of those at the lower levels of organizational hierarchies. We published a book from this research, FastLane: Managing Science in the Internet World (Johns Hopkins University Press, 2015).
Sessions four and six of the HBS conference explored “Oral History and the Creation of Knowledge” in two large regions, Africa, and Latin America, respectively. These sessions served as broad reminders of how archival infrastructure is sparser in some regions of the world, and thus, the critical role oral history and ethnography can play in understanding business and culture is heightened.
Political scientist and Vice Dean of Education at the University of Toronto Antoinette Handley provided an insightful talk on “African Business Elites: Changing Perceptions of Power.” Laurent Beduneua-Wang offered an intriguing examination of “Ethnography and Oral History in Morocco.” While HBS’ Marlous van Waijenburg spoke broadly on “Capturing African Histories and Experiences,” a talk which by admission and intent was not so much on oral history. Instead, it was an expert high-level overview of issues in African history and historiography and thus provided rich context.
On the topic of Latin America, Andrea Lluch gave another terrific paper, “Managing Business in Unstable Contexts,” where she focused on the instability of currency in Argentina and how adjustments in the timing of purchases, planning, and salary increases were used by consumers and producers to cope with the seemingly untenable circumstances of frequent hyperinflation. Marcelo Bucheli a business historian and political economy specialist at the University of Illinois, in turn, spoke on “Political Uncertainties in Emerging Markets” in Latin America. Finally, Miguel A. Lopez-Morell (University of Murcia) presented a co-written paper he did with business historian Bernardo Batiz-Lazo (Northumbria University) entitled, “Digital Conquistadors,” contributing strongly to our understanding of history and historiography of banking in Latin America.
Oral History and Pedagogy
The penultimate session, number five, “Employing Oral History in Teaching” was a particularly important one to the event. Tarun Khanna convened this session. In general, oral history is grossly underutilized in undergraduate and graduate education, as well as high school—both from the standpoint of drawing on oral histories to instruct, as well as teaching the skills and techniques to conduct oral history well. This session explored various strategies for utilizing and enhancing skills for oral history in education. Chinmay Tumbe of Indian Institute of Management spoke on “Best Practices for Oral History Teaching and Collection Development.” Next Sudev Sheth offered a paper entitled “Teaching Global Leadership,” and how oral history can be a helpful tool. Lastly, Arianne Evans of Harvard’s Graduate School of Education presented “Incorporating Oral History into High School Pedagogy.
“Creating Emerging Markets”
From start to finish, this was a well-designed event where themes of methods, gender, geographies, research uses, and educational uses all came together to provide a coherent and vibrant whole. Discussions following the papers after each of the six sessions, as well as during the breaks and meals, were lively. We also all received a copy of Geoffrey Jones and Tarun Khanna’s Leadership to Last: How Great Leaders Leave Legacies Behind. It is a 330-page book with a paragraph-long biography on each interviewee, and then edited passages from forty-four interviewees selected from the “Creating Emerging Markets” Oral History Project.

This book serves as both a source of management lessons from the past as well as a glimpse into a significant project and its resources. For business historians and social science researchers, these passages are short and make a reader wonder about the context of the whole interview. That said, the interviewer questions (from Khanna and other researchers) are well-constructed to elicit insightful responses. Without question, it leaves you wanting to read more. While this might seem a liability, it is not. I am certain one of Jones’ and Khanna’s goals is to bring attention to the larger project and its resources, and for me, it did just that. Further, I especially like the choices of the seven themes/chapters, each with five to eight interviewees apiece:
- Managing Families
- Committing to Values
- Innovating for Impact
- Contesting Corruption
- Challenging Gender Stereotypes
- Promoting Inclusion
- Creating Value Responsibility
In reading this terrific book, as well as visiting other select oral histories on the “Creating Emerging Markets” website, the extensive research preparation of the interviewers stands out. In our program at CBI, modeled on leading programs at the University of California, Berkeley, and Columbia University, this continues to be our practice as well. Our extensive preparation is what produces four decades of what we have long termed “research-grade” oral histories. We believe this extensive commitment to research preparation and having appropriate, well-trained, and prepared interviewers is key to our success with securing and delivering upon oral history sponsored research project support from NSF, Sloan, NEH, DOE, ACM, IBM, and others.
“Creating Emerging Markets” is producing similar research infrastructure and resources, as they also invest in video and snippets which add so much to visibility and educational use— “research and educational-grade interviews” perhaps?
Public Goods
While we are not doing the production-quality video at CBI, I serve on the History Committee of the leading professional organization for computer science the Association for Computing Machinery (ACM), and for that organization we are doing production video oral histories with Turing Award winners (equivalent to the Nobel Prize for computer science) and video snippets from each of these. This undoubtedly makes them more useful in computer science education, as well as the history of computing and software. With “Creating Emerging Markets” the interviews are rich for research and education in history, sociology, management, international studies, African studies, Latin American Studies, Asian Studies, and other disciplines.
A term Geoffrey Jones used repeatedly at the conference is that their “Creating Emerging Markets” Project is producing “public goods.” I would agree that the term makes sense and is fitting for a business school and business history (I have an MBA in addition to a Ph.D. in history). When I have my CBI and historian, humanities, and social science hats on, it is what I might call public resources or historical research infrastructure—that is how I commonly speak about CBI’s Oral History Program (and archives) and the public resources it produces (full transcripts of many hundreds of two-to-sixteen-hour interviews and 320 extensively processed archival collections). “Public goods” works very well for the “Creating Emerging Markets” Oral History Project as the video snippets are engaging for audiences in education, corporate education, and the wider public who have an interest.
In its dozen years “Creating Emerging Markets” has produced 181 oral histories with interviews from thirty-four countries and its site gets 80,000 hits per year at present. The interviews on the Global South span such topics as leadership, governance, business education, family business, race, gender, political economy, and more. A link to “Creating Emerging Markets” is in the bibliography, and I highly recommend visiting this incredible resource. For historians of business and management scholars of the Global South, it is tremendously valuable. And given the well-selected video snippets, it will appeal broadly.
Oral history theory, practice, collections, and publications remain rare in emerging markets. Existing projects and the surrounding literature on both interviews and methods/techniques tend to focus more on politics and culture than business and enterprise. For instance, there are such books as David Carey Jr.’s Oral History in Latin America: Unlocking the Spoken Narrative, Anindya Raychaudhuri’s Narrating South Asian Partition: Oral History, Hassimi Oumarou Maïga’s Balancing Written History with Oral Tradition: The Legacy of the Songhoy People, and Patai Daphne. Brazilian Women Speak: Contemporary Life Stories. As such “Creating Emerging Markets,” importantly, is filling an important void, as it also does much more.
“Creating Emerging Markets” is creatively and expertly building new possibilities in the business oral history space and, importantly, intersecting with the targeted geography of the Global South. Through its use of experienced and diverse business historians, management scholars, and social scientists as interviewers, through the video teams and well-selected snippets to highlight, through the development of enhanced configurable and automated searching and generation techniques, and through the edited transcripts it is innovating in methods, tools, and thematic and geographic targets in ways that strongly advance research and education opportunities in understanding emerging markets and their political economy and cultural milieu.
HBS’ “Oral History and Business in the Global South,” was such an intellectually delightful event. It worked terrifically as an engaging conference on its own and also as—along with their 2022 book Leadership to Last—a coming out party for an extremely important project, “Creating Emerging Markets,” that is developing and making public wonderful research and educational resources with enormous possibilities on parts of the world and leaders and workers who contribute so much and too often are ignored. The quality of the scholarship presented, the quality and importance of the “Creating Emerging Markets” Project, and the intellectual generosity of the conveners, presenters, and audience made it special to be part of this lively and vital conversation.
HBS’ Baker Library and Its Historical Research Gems
All the events were at HBS’ Chao Center, including a reception and catered Indian cuisine dinner after the first day of the conference. About half of the two dozen or so presenters and attendees took part in a fantastic tour of Baker Library led by Laura Linard. The sublime special collections include unique archives—corporate records, annual reports, ledgers, personal papers—extensive rare books, an art collection, and much more. The records on business history date back to the 14th century, with amazing materials in that century and each one since. The thoughtfully presented display cases, elegant reading room, and art throughout the public areas of Baker Library add much to the intellectual and aesthetic allure.
In 1819 the Ecole Spéciale de Commerce et d’Industrie (now the ESCP Business School), was established in Paris. It often is credited as the first business school in the world. Harvard Business School, established in 1908, has the distinction as the first to introduce the standard Master of Business Administration (MBA) degree. Through its incredible faculty, its methods, and its unequaled published series of case studies that are used far more than any other series in business schools globally, Harvard has an outsized impact on business and management education and educating and influencing future leaders in the U.S. and around the world. The Baker Library documents this institutional history, as it also documents business history globally.
We took the elevators down to the closed stacks and saw where the Alfred D. Chandler Collection and other archival collections are held. Of particular interest to computer historians, the library has the personal/business papers of legendary Digital Equipment Corporation founder and longtime leader Kenneth Harry Olsen. Laura, in addition to giving us the group tour, was kind enough to meet with me for an hour afterward. We discussed archives and history and the respective missions of our institutions, exploring if there were areas where we might be helpful to one another in collecting. It was a wonderful discussion and the perfect ending to two engaging and intellectually exciting days at Harvard Business School.
Bibliography
Carey, David Jr. (2021). Oral History in Latin America: Unlocking the Spoken Narrative. (Routledge).
“Charles Babbage Institute for Computing, Information and Culture Oral History Program and Resources.” CBI Oral Histories | College of Science and Engineering (umn.edu)
“Creating Emerging Markets,” Harvard Business School. “Creating Emerging Markets” - Harvard Business School (hbs.edu)
Jones, Geoffrey, and Tarun Khanna. (2022). Leadership to Last: How Great Leaders Leave Legacy’s Behind. (Penguin Business).
Maïga, Hassimi Oumarou. (2012). Balancing Written History with Oral Tradition: The Legacy of the Songhoy People (Routledge).
Misa, Thomas J., and Jeffrey R. Yost. (2015). FastLane: Managing Science in the Internet World. (Johns Hopkins University Press).
Patai, Daphne (1988). Brazilian Women Speak: Contemporary Life Stories. (Rutgers University Press).
Pruitt, Bettye, with the assistance of Jeffrey R. Yost. (1998) Timken: From Missouri to Mars—A Half Century of Leadership in Manufacturing. (Harvard Business School Press).
Raychaudhuri, Anindya. (2019) Narrating South Asian Partition: Oral History (Oxford University Press).
Sheth, Sudev, Geoffrey Jones and Morgan Spencer. (2021). Business History Review 95:3 (Autumn): 483-515.
Yost, Jeffrey R. (2017). Making IT Work: A History of the Computer Services Industry (MIT Press).
Yost, Jeffrey R. “Harvard Business School’s “Oral History and Business in the Global South”: A Review Essay and Reflection.” Interfaces: Essays and Reviews on Computing and Culture Vol. 5, Charles Babbage Institute, University of Minnesota, 38-48.
About the author: Jeffrey R. Yost is CBI Director and HSTM Research Professor. He is Co-Editor of Studies in Computing and Culture book series with Johns Hopkins U. Press and is PI of the new CBI NSF grant "Mining a Useful Past: Perspectives, Paradoxes and Possibilities in Security and Privacy." He is author of Making IT Work: A History of the Computer Services Industry (MIT Press), as well as seven other books, dozens of articles, and has led or co-led ten sponsored history projects, for NSF, Sloan, DOE, ACM, IBM etc., totaling more than $2.3 million, and conducted/published hundreds of oral histories. He serves on committees for NAE, ACM, and IEEE, and on multiple journal editorial boards.

Management thinkers tend to fade from popularity when a new management trend arrives. These new practices appear and are followed with endless rounds of meetings, new buzzwords for the office cronies, and extra work that ends up driving employees crazy or their company out of business. But amidst all the changes in management styles, one voice kept its calm, soothing tone, with no buzzwords just firm guidance, through six decades. That voice was Peter Drucker’s.
For Drucker, management is a social function and a liberal art (Drucker 1989). He was amazed at the speed with which management emerged and became an integral part of society. In 1989 he reflected on the institution of management and how rarely in human history other institutions have been so transformative, so quickly, that in less than 150 years they have created a new world order and provided a new set of rules (Drucker 1989).
Drucker stayed relevant and was part of every manager’s vocabulary through his extensive writing and strong presence in mass media. He was the author of 39 books, translated into 36 different languages (O’Toole 2023), and he also wrote many columns for the Wall Street Journal, Harvard Business Review, The Atlantic Monthly and The Economist. In his management books, he consistently discussed, not just the function of managing, but also its social impact. It was clear to Drucker that management was so pervasive as a social function, that it became its Achille’s heel. He wanted to bring to the attention of managers that management must be accountable, to point out the sources of management’s power, and its legitimacy (Drucker 1989).
The goal of this essay is to document the enduring legacy of Peter Drucker for management theory. We aim to evaluate his clarity of vision, especially regarding the information revolution he foresaw very early, before computers were fully adopted into organizations. We use primary and secondary sources to assess how we are confronting and overcoming the management challenges that Drucker foresaw for this new century. First, we present Peter Drucker, the person, then we discuss the historical validity of using the term “guru” when referring to Drucker. Next, we present a review of Chapter 4, “Information Challenges” of his 1999 book, Management Challenges for the 21st Century to evaluate his incisive commentary regarding the impact of information, information systems and information technology in institutions and society. Finally, we conclude with a short discussion about where the Information Revolution has taken us, as of 2023.

Peter Drucker, The Person
Peter Ferdinand Drucker (November 19, 1909 – November 11, 2005) was born in Vienna under the Austro-Hungarian Empire, where his father, Adolf Drucker, was a high-level civil service lawyer. His household was a place where intellectuals and high government officials gathered regularly, among them Joseph Schumpeter (Austrian-born, American economist and Harvard University Professor), and his uncle Hans Kelsen (Austrian jurist and philosopher). At eighteen, after finishing his studies at Döbling Gymnasium, and having difficulties finding a job in post-World War I Vienna, he decided to move to Hamburg, Germany
Drucker became an apprentice in a cotton trading company. He started writing for the Austrian Economist (Der Österreichische Volkswirt) which gave him some credentials and the confidence to pursue a career as a writer. Shortly after, he moved to Frankfurt to work at a daily newspaper. He enrolled at the University of Frankfurt where he earned a doctorate in International and Public Law at the age of 22.
He remained in Frankfurt for two more years; the rise to prominence of National Socialism and Hitler were events that caused him to leave. Some Austrians were becoming infatuated by the transformation of Germany; Drucker was not one of them. He decided to go to London in 1933, where he worked first for an insurance company and then as chief economist for a private bank. While in London, he married an old friend from the University of Frankfurt, Doris Schmitz. Together they emigrated to the United States in 1937.
The Drucker’s lived in Bronxville, New York for five years. In 1942, they moved to Bennington, Vermont where Drucker held a position at Bennington College as a professor of politics and philosophy. In 1950 they moved again, this time to Montclair, New Jersey where Drucker became a professor of management at New York University, a position he held for 20 years. In 1971, he became the Clarke Professor of Social Science and Management at Claremont Graduate School (Now Claremont Graduate University), a position he maintained until his death. He was instrumental in the development of one of the United States’ first executive MBAs for working professionals. Marciariello, in writing about Drucker’s driving force, recognizes the vast influence history, and his own early life experiences in Austria and Germany during the World Wars, had on his thinking to empower citizens of free societies, “so they would never be tempted to turn to authoritarian substitutes” (Marciariello 2014, xviii).
Peter Drucker, The “Guru”
Recognizing that “Guru” is an appropriate term from Hinduism, it has now lost its power in management studies where influencers may now be used. Historically, the term has a very precise place when discussing Drucker. As historians, we bring it forward in this essay, fully recognizing that for today’s readers it may have unsavory connotations, and it does not fully comply with our current ethical values. We hope that readers may see the value of its usage without compromising any aspect of equity, diversity, and inclusion.
Drucker is considered one of the most influential management thinkers ever. He was called the “leading management guru” (Harris 2005) and an “uber-guru” (Wooldridge 2009) after his death, and was influential from the time his first book on management was published in 1954. Over the years, he authored more than 25 books that have impacted the shaping of the modern corporation. In the process, he established himself as someone who knew managers, not just theorized about them.
Brad Jackson (2001) observed the management “guru” fad since 1994, originally, as a manager seeking help and guidance, later as an adult educator facilitating access to lectures by “gurus” and finally as a researcher seeking to add to the debate about “guru” theory. He identifies the “guru” fad as a phenomenon that began during the 1980s in the United States but then expanded throughout the rest of the world. He also documents the backlash during the mid-1990s against the “gurus” themselves, but mostly against management fads or fashions. He identifies rhetoric as the key element that ‘makes’ a management “guru.” He also invites his readers to deconstruct this rhetoric and demystify the ‘doctrines of salvation’ offered by those “gurus.”
From Jackson’s analysis and critique, we see Drucker’s rhetoric not as a ‘doctrine of salvation’ but as a conversation that is open, full of possibilities, emerging from his own experiences. Drucker practiced management. He was a keen observer of his actions and was able to write about them clearly and convincingly. We can think of his writing as a report from the field. When he wrote about Ford Motor Co., Sears Roebuck, or IBM (Drucker 1954), he was, in essence, writing business history and inviting his readers to witness history with him. Then, after demonstrating the practice of management in these world-renowned organizations, he invited us to consider the social impact of management decisions.
Perhaps the aspect that resonated the most with his readers was his absolute conviction that freedom and liberty are invaluable and not always guaranteed. Something he wanted all of us never to forget.
“In a free society the citizen is a loyal member of many institutions; and none can claim him entirely or alone. In this pluralism lies its strength and freedom. If the enterprise ever forgets this, society will retaliate by making its own supreme institution, the state, omnipotent” (Drucker 1954, 460).
This was so important for Drucker that Jim Collins, popular business consultant and author of Built to Last: Successful Habits of Visionary Companies (2004), when addressing participants at the Drucker Centennial on November 2, 2009, declared, “Drucker contributed more to the triumph of freedom and free society over totalitarianism than anyone in the 20th century, including perhaps Winston Churchill” (Collins 2009). His legacy is well recognized, not only by those who worked closest to him (The Claremont Graduate University named their business school after Drucker) but all over the world. Because of this, people have been joining the Peter Drucker Institute which was created in 2006 as an extension of the Drucker Archives with the mission of “Strengthening Organizations to Strengthen Society”. They convene annually to continue Drucker’s conversations. They not only want to look back to Drucker’s writings, but they also want to look forward to new ideas that can be generated out of his work. In many ways, that is in essence what gurus are, guiding lights into the future. A testament to many, Drucker is the greatest source of managerial wisdom.

Management Challenges for the 21st Century
At age 90, beyond the expected lifespan of most people, Drucker published his 34th book. In his lifetime, he witnessed an enormous transformation not only in Europe, but all over the world: two World Wars, the rise and fall of the Soviet Union, the construction and fall of the Berlin Wall, the Cold War, the emergence of China, and the ossification of many American institutions. He knew that he needed to warn his readers about what was coming in the new millennium. He started the conversation at the beginning of the 1990s with The New Realities (1989) and decided to continue the conversation regarding the challenges management would face in the new century with Management Challenges for the 21st Century (1999).
Drucker sought to discuss the new paradigms of management and how these paradigms had adapted and changed toward the end of the 20th century. He wanted us to change our basic assumptions about the practice and principles of management. He concentrated on explaining the new information revolution by discussing the information executives need and the information executives owe. He brought the discussion of the knowledge worker productivity to the front and center.
Information Challenges
Drucker starts Chapter 4 of his 1999 book with a declaration:
“A new Information Revolution is well underway. It has started in business enterprise, and with business information. But it will surely engulf ALL institutions of society. It will radically change the MEANING of information for both enterprises and individuals.”
This declaration identifies two issues that we can use to check how accurate he was in his predictions. The first issue is Drucker’s claim that the information revolution will affect ALL institutions of society, and the second is about the changing MEANING of information.
Issue I: Institutions
If we were to look now for institutions that have not been affected by the information revolution, we would be hard pressed to identify one. Governments all over the world now have an online presence that was not in evident at the end of the 20th century, even in countries with small populations like Tuvalu, Palau, San Marino, Liechtenstein, and Monaco; as well as those countries with the smallest GDP, including Syria, Tuvalu, Nauru, Kiribati, and Palau. Investigations of the impact of information technology on governments have ranged from the potential of globalization facilitated by information technology and calling into question the very existence of the nation state (Turner 2016), to the influence of e-commerce on the ability of governments to raise tax revenue (Goel and Nelson 2012), and the threat to critical national infrastructures from cyber threats (Geers 2009). And more recently, how social media may facilitate social upheaval and revolution such as was experienced during the Arab Spring (Bruns, Highfield and Burgess 2013).
Businesses have been not only transformed, but also created and help bring about this Information Revolution (Google, Facebook -now Meta, Twitter -now X, Zoom, etc.) Businesses are now more prone to be impacted by cyber security threats (Kshetri 2009). Educational institutions have been transformed with massive open online courses (MOOCs). Online learning has increased to be the way most institutions communicate with their students; assignments are delivered through Learning Management Systems; and recruitment, application, and acceptance are all web-based. Banking services have moved online as people can even deposit cheques by simply taking a photograph within their banking app. Legal institutions have developed online resources that include among others the creation of Blawgs (internet-based blogs dealing with topics related to Law), and other resource repositories. The mass media has been particularly impacted. The demise of newspapers and the emergence of disinformation with ‘fake news’ or ‘alternative facts’ are just two examples of how much the information revolution has transformed these institutions.
Health Institutions have been forced to transform to deal with the explosion of medical information available on the web. Popular sites include PatientsLikeMe.com, and a multitude of communities around specific diseases: WeAreLupus.org, WeAreFibro.org (for fibromyalgia), WeAreHD.org (Huntington’s disease), etc. have switched over.
The last group of institutions we discuss is the military, obviously a group for which it is more difficult to get information since they like to keep it a secret as part of their raison d’être. At the same time, military organizations are part of the government, and as such they have a mandate to have a presence online. The US Army has its own domain (.mil), due to its heavy involvement in the development of internet technologies through partnering with research centers and universities.
Because Drucker focused on the wider societal impact of management, we are also able to examine how the information revolution has affected personal relationships through platforms like Facebook (over 3 billion users), WhatsApp (2 billion users), Instagram (1.4 billion), TikTok (1 billion), MeetUp (60 million), and others for dating and courtship. According to Cesar (2016), online dating services generate $2 billion in revenue per year in the US alone and expand at an annual rate of 5% per year between 2010 and 2015. In 2016, a study by the Pew Research Centre (Smith 2016) revealed that 15% of American adults reported using online dating sites and/or mobile dating apps and, further, that 80% of Americans who had used online dating agreed that it was a good way to meet people.
The study’s author noted that growth in the use of online dating over the previous three years had been especially pronounced for two groups that had not historically used online dating – the youngest adults (18 to 24 years of age) and those in the late 50s and early 60s. Some of the increase in use is credited to the use of gamification by apps such as Tinder, which makes choosing a ‘dating partner’ as easy as swiping to the left or right on a mobile device. Tinder now operating in 196 countries, reports its users make an average of 1.6 billion swipes per day (Tinder 2024). Lest, we think the only impact has been positive, recent academic research has shown the negative impact of partner phubbing (phone snubbing) on depression, relationship satisfaction and personal well-being (Roberts and David 2016).
It is clear from the preceding discussion that Drucker was very accurate in his declaration regarding ALL institutions being impacted by the information revolution.

Issue II: Meaning
A less obvious analysis regarding the MEANING of information is possible only by pointing out what the meaning of information was before the revolution started. Meaning is essentially a concern of Semiotics. One of the greatest semioticians of all time, Umberto Eco, was a proponent of information as a way of being human. In his essays Open Work (1962), Minimal Diary (1963) and Apocalyptic and Integrated (1964), he talks about a dichotomy between optimistic and pessimistic intellectuals who either reject or accept mass culture.
Eco finds the term information to be an ambiguous one. What interested Eco about information theory is the principle that the quantity of information (as opposed to the meaning) contained in a message is in inverse proportion to its probability or predictability, something that to him resembled the effect of art, particularly modern art. Thus, Eco argues, art in general may be conveying a much higher degree of meaning than more conventional kinds of communication. He argues that:
“…the quantity of information conveyed by a message also depends on its source … information, being essentially additive, depends on its value on both originality and improbability. How can this be reconciled with the fact that, on the contrary, the more meaningful a message, the more probable and the more predictable its structure?” (Eco 1989, 52).
It was clear enough for Eco that “meaning and information are one and the same thing” (Eco 1989, 53). He is puzzled by the practicality under which the new information revolution started. The intellectuals behind the new information age, in a very myopic, practical way created the Millennium Bug (or the Y2K Bug) not due to ignorance, but out of lack of vision. Eco was puzzled by programmers who didn’t anticipate the date problem 50 years down the road, but the Millennium Bug was a business decision to keep costs down when digital storage space was highly expensive.
Eco’s sense of amazement is also about the greatest repository ever built, the World Wide Web. He is especially concerned about how digital information is never forgotten, allowing us to re-interpret it, constantly, giving it a sense of fluid meaning, until we reach information overload: “To my mind, to have 14 million websites is the same as having none, because I am not able to select” (Eco et al. 1999, 192).
That is a good way to start to see those who immediately accepted the information revolution, a.k.a. the information age, and those who dismissed it while continuing their existence without questioning the impact that information would have on their lives. Among the ‘integrated,’ John Seely Brown, along with Paul Duguid, published The Social Life of Information (2000) to document the meaning of information in our social life. They start by reminding us of how, at one time, the lack of information was a problem: “It now seems a curiously innocent time, though not that long ago, when the lack of information appeared to be one of society’s fundamental problems” (Brown & Duguid 2000, 12).
They document how chronic information shortages threatened work, education, research, innovation, and economic decision-making. They remind us throughout the book that, “we all needed more information” as well as how “for many people famine has quickly turned to glut.” This is a good indication that the meaning of information has changed for most of us.
Issue III: Concepts
Drucker also indicates that the information revolution is “a revolution in CONCEPTS” (Drucker 1999, 97); by this he meant that it was not about Information Technologies (IT), Management Information Systems (MIS), or Chief Information Officers (CIOs). He accused the information industry—the IT people, the MIS people, the CIOs—of failing to provide information by being more interested in the technology than the information side of their mandate.
“So far, for fifty years, Information Technology has centered on DATA—their collection, storage, transmission, presentation. It has focused on the ‘T’ in ‘IT.’ The new information revolutions focus on the ‘I.’ … What is the MEANING of information and its PURPOSE?” (Drucker 1999, 97).
He was correct on some issues but missed one of the biggest transformations of this industry: going from IT to information and communication technology (ICT) with the arrival of Apple’s iPhone in 2007. Indeed, people were not looking for information when buying an iPhone, but this piece of technology redefined our interaction with technology, from keyboard-enabled communication to a freer way to get what we want, anywhere, anytime. Not only that, but this device was also so revolutionary that it reshaped many industries. The mobile phone giants, Nokia, Blackberry, Samsung, etc., were not prepared, and their businesses were completely changed. Digital cameras have almost disappeared since the smartphone allows us to always have a camera with us. Personal Digital Assistants (PDAs), launched in 1996, were required to supplement the capabilities of mobile phones, but disappeared as well since they were no longer needed when carrying a smartphone. This led to the demise of world leader, Palm Inc. Even Apple’s own iPod was cannibalized by the iPhone since people could now use their phones to listen to their iTunes collections, and after the rise of Spotify, streaming music is the new way to listen to it.
Historically speaking, the information industry needed to concentrate on technology first since it emerged in a world of analog technologies. To go fully digital, a completely new set of skills was needed. Since everything was new, there were several options tested, and if companies jumped too early into one, they ran the risk of becoming obsolete very quickly. The race for the personal computer left many big players, including IBM, with serious losses. In those fifty years that Drucker mentions in his statement, the world went from very expensive room-sized mainframe computers to affordable portable laptops; from magnetic tapes to punched cards to 5¼” and 3½” floppy disks; from 2,000 to 760 million instructions-per- second. The industry needed to be focused on technology until the technology was good enough to deliver that sense of instant connectivity, 24/7, anywhere. Therefore, businesses needed to play a game of either wait-and-see or jump-on-board into an unknown future. Following Rogers’ (1962) Diffusion of Innovation Theory: Innovators à Early Adopters à Early Majority à Late Majority à Laggards.
The aspect that Drucker wanted to highlight in his assessment is that users, especially executive users, needed to engage in the information revolution not from a perspective of being seduced by new tools, but by being able to do things that were not possible before without these technologies. That is why he stressed the importance of concepts, concepts that would emerge only by questioning what those users were doing, “top management people during the last few years have begun to ask, ‘What information concepts do we need for our tasks?’” (Drucker 1999, 100).
In answering that question, we have seen the transformation of business computing purpose from Decision Support Systems (DSS) to Executive Information Systems (EIS), to Business Intelligence (BI), to the current Business Analytics (BA). Also, the role of data as a by-product of Transaction Processing Systems (TPS), has transformed into data as an asset, and data as the new oil. Are these new concepts or just slogans?
To grasp the sense in which Drucker used the term ‘concept’ in his analysis of the information revolution, perhaps is important to remember that he taught philosophy at the beginning of his career as an academic at Bennington College. In his autobiography, Druker writes about Karl and Michael Polanyi, and even though he does not mention Ludwig Wittgenstein specifically, Wittgenstein was living in Vienna at the same time as Peter Drucker was. This time has been documented as the first Vienna Circle, a time when many revolutionary new ideas in philosophy were emerging. More than an etymological definition we need an epistemological one of ‘concept’ to capture the sense that Drucker may have had when writing about informational challenges.

Peacocke (1996) discusses “concepts” as a way of thinking about something. One object in particular, a given property, a relation, perhaps an entity. He emphasizes that concepts have to be distinguished from stereotypes. He reminds us that while the theory of concepts is part of the theory of thought and epistemology, the theory of objects is part of metaphysics and ontology. “…a theory of concept is unacceptable if it gives no account of how the concept is capable of picking out the objects it evidently does pick out” (Peacocke 1996, 74).
Even though Drucker is writing about the information revolution at the end of the 20th century, he was very clear, since The Practice of Management, that information, to him, is “the tool of the manager” (Drucker 1954, 412). He explains what that concept means to him through the way he explains what he means by listing the collection of ‘objects’ he picks out:
“The manager has a specific tool: information. He does not ‘handle’ people; he motivates, guides, and organizes people to do their own work. His tool – his only tool – to do all this is the spoken or written word or the language of numbers. No matter whether the manager’s job is in engineering, accounting, or selling, his effectiveness depends on his ability to listen and to read on his ability to speak and to write. He needs skill in getting his thinking across to other people as well as skill in finding out what other people are after … must understand the meaning of the old definition of rhetoric as ‘the art which draws men’s hearts to the love of true knowledge’” (Drucker 1954, 413).
The choices are clear. For Drucker, from the time he started writing about the practice of management up to his discussion of the information revolution, reading, writing and arithmetic, and rhetoric, are the concepts that make information useful to managers. After nearly fifty years, he recognizes that not much has changed for executives:
“In business across the board, information technology has had an obvious impact. But until now that impact has been only on concrete elements—not intangibles like strategy and innovation. Thus, for the CEO, new information has had little impact on how he or she makes decisions. This is going to have to change” (Drucker 2002, 83).
Perhaps for no one else but Drucker, at the dawn of the 21st century it was clear that data alone would not suffice to compete and win in the new economy. Drucker puts the onus on each knowledge worker by correctly pointing out that “no one can provide the information that knowledge workers and especially executives need, except knowledge workers and executives themselves” (Drucker 1999, 124).
Conclusion
Drucker was correct when in 1999 he warned us of the challenges we would be facing in the 21st century, especially those regarding the new information revolution. Looking at the three issues that he brought to our attention: Institutions, Meaning and Concepts, we can see that in the last 23 years, all of them have had a transformation due to the ICTs that have emerged (and continue to emerge). Institutions now have a digital reality that keeps them present to their constituents 24/7, anywhere and everywhere.
The meaning of information, especially the issues of information overload, misinformation and disinformation is a constant threat to institutions and people. Privacy and security online are now aspects that were formerly not present in the digital world of management. Willingly or unwillingly, we must recognize, for example, that X (formerly Twitter) is an essential tool to take the pulse of politics. How would the world of business survive the 2020 pandemic without the emergence of Zoom?
Can concepts help us retake control of the meaning of information? That is something that the new generation of managers will have to decide. The generation that has grown up digital is starting to take its place in the workforce, and we will have to wait and see if they take this control back to its rightful owners, the people.
Drucker had a view of society that no longer describes the society we live in. He was very optimistic about what individuals get by participating in social groups. His revolution was a gentle one offering many advantages not only to managers and organizations but to simple individuals. Something that is no longer true. The revolution we are witnessing is a harsher one, with huge inequalities generated between those with access to these technologies and those without; corporations that are valued by intangibles with little regulation; the emergence of Neoliberalism. A revolution biased against marginalized groups either by race, gender, disability, or access to education.
Looking at primary and secondary sources, we have opened a conversation regarding how organizations are confronting the challenges that Peter Drucker foresaw at the close of the 20th century. At least for us, from the perspective of the information revolution, we think that we are doing what is needed to conform to the demands of the new realities. But there is still much work to be done and having Drucker’s legacy in his writing is reassuring.
Bibliography
Bruns, A., T. Highfield and J.E. Burgess (2013). “The Arab Spring and social media audiences: English and Arabic Twitter users and their networks,” American Behavioral Scientist, 57, (7), 871-898.
Brown, J. S., and P. Duguid. (2000). The Social Life of Information (Harvard Business School Press).
Cesar, M. (2016). “Of Love and Money: The Rise of the Online Dating Industry,” http://www.nasdaq.com/article/of-love-and-money-the-rise-of-the-online-dating-industry-cm579616 (accessed February 3, 2024).
Collins, J. (2009). Address, available as a video at: www.druckerinstitute.com/peter-druckers-life-and-legacy/tributes-to-drucker (accessed January 19, 2024).
Drucker, P.F. (1954). The practice of management (Harper & Brothers).
Drucker, P.F. (1978). Adventures of a Bystander (Harper & Brothers).
Drucker, P.F. (1989). The New Realities: In Government and Politics, in Economics and Business, in Society and World View (Harper & Row).
Drucker, P.F. (1999). Management Challenges for the 21st Century (Harper-Business).
Drucker, P.F. (2002). Managing in the Next Society (Truman Talley Books – St. Martin’s Press).
Eco, U. (1989). The Open Work (Harvard University Press).
Eco, U., S.J. Gould, J.C. Carrière, and J. DeLumeau (1999). Conversations about the end of time (Penguin).
Geers, K. (2009). “The Cyber Threat to National Critical Infrastructures: Beyond Theory,” Information Security Journal: A Global Perspective, 18, (1), 1-7.
Goel, R.K. and M.A. Neilson (2012). “Internet Diffusion and Implications for Taxation: Evidence from U.S. Cigarette Sales, Internet & Policy, 4, (1), 1-15.
Harris, K. (2005). “Peter Drucker, leading management guru, dies at 95, 11 November,” available at: www.bloomberg.com/apps/news?pid=newsarchive (accessed January 15, 2024).
Jackson, B.G. (2001). Management Gurus and Management Fashions, London: Routledge.
Kshetri, N. (2009). “Positive Externality, Increasing Returns and the Rise in Cybercrimes,” Communications of the ACM, 52 (12), 141-144.
O’Toole, D. (2023). The Writings of Drucker, in The Daily Drucker, November 12, 2023, https://dailydrucker9.wordpress.com/ (accessed February 20, 2024).
Maciariello, J. A. (2014). A year with Peter Drucker (Harper-Business).
Peacocke, C. (1996). Concepts. In Dancy & Sosa (eds.) A companion to Epistemology, The Blackwell Companions to Philosophy (Blackwell).
Ramirez, A. (2020). “Of Bugs, Languages, and Business Models: A History,” Interfaces: Essays and Reviews in Computing and Culture, Vol. 1, Charles Babbage Institute, University of Minnesota, May 2020: 9-16.
Roberts, J.A. and M.E. David (2016). “My life has become a major distraction from my cell phone: Partner phubbing and relationship satisfaction among romantic partners,” Computers in Human Behavior, 54, 134-141.
Rogers, E. (1962). Diffusion of Innovations (Free Press).
Smith, A. (2016). 15% of American Adults Have Used Online Dating Sites or Mobile Dating Apps, 11 February, available at: http://www.pewinternet.org/2016/02/11/15-percent-of-american-adults-have-used-online-dating-sites-or-mobile-dating-apps/ (accessed February 3, 2024).
Tinder (2024). About Tinder, available at: https://www.gotinder.com/press?locale=en (accessed February 3, 2024).
Turner G. (2016). “The Nation-State and Media Globalisation: Has the Nation-State Returned — Or Did It Never Leave?” In Flew T., Iosifidis P., Steemers J. (eds) Global Media and NationalPolicies. (Palgrave Macmillan), 92-105.
Wooldridge, A. (2009). Peter Drucker: uber-guru, paper presented at the 1st Global Peter Drucker Forum, Vienna, 19-20 November, available at: www.druckersociety.at/repository/abstracts.pdf (accessed January 6, 2024).
Alex Ramirez (March 2024). “A Revolution: Drucker Saw it Coming.” Interfaces: Essays and Reviews on Computing and Culture Vol. 5, Charles Babbage Institute, University of Minnesota, 23-37.
About the author: Alejandro Ramirez is an Associate Professor of Business Analytics and Information Systems at the Sprott School of Business – Carleton University in Ottawa, Ontario, Canada. He has a PhD in Management – Information Systems (Concordia), an MSc. in Operations Research & Industrial Engineering (Syracuse), and a BSc. In Physics (ITESM). He has been active with the Business History Division of ASAC since 2012 and has served as Division Chair and Division Editor. He is interested in the History and the stories of Information Systems in Organizations.
In the past five years, corporations have been pressured to stop just focusing on stockholders and instead also pay attention to the needs of other stakeholders: employees, communities, indeed entire societies. Many high-tech firms, and notably social media ones, are being criticized for letting fake facts proliferate threatening the very foundations of democracy and civic behavior, such as Facebook (Meta) and Twitter (X), while others are accused of treating their employees almost as if they worked in sweatshops, such as Amazon. They are not allowed to hide behind new names, such as Meta and X, and regulators are chasing them all over the world for their near monopolistic dominant positions or for treating one’s personal data in a cavalier fashion. So many IT firms are big enough that they actually affect political and social behavior across many countries. In short, they no longer are just companies within some vast economy, rather now pillars of the societies in which they operate. That is largely why so many in the public are demanding that (a) they respect one’s privacy and (b) that they take seriously the values of their customers (e.g., being environmentally friendly, inclusive in serving and hiring myriad racial, ethnic-identifying people).
CEOs are pledging to do better and to serve a broader range of stakeholders, while some are holding out. Nonetheless, it seems every high-tech firm almost anywhere is under the microscope of regulators, legislators, interest groups, customers, and societies at large. Historians, economists, business school professors, sociologists, and—just as important—some wise and experienced business leaders understand that how to deal with stockholder vs. stakeholder issues boils down to corporate values, policies, how it treats customers and employees, and their commitments to society—in short to corporate cultures. So many high-tech firms are so new, however, that they are, to be blunt about it, borderline clueless on how to shape, implement, and change their corporate cultures. Yet the growing empirical evidence is that managing corporate cultures may be more important than coming up with some clever business (product or service) strategy. College students founded Facebook in 2004, becoming the poster child for a firm that many feel is yet to be run by experienced executives, specifically Mark Zuckerberg, one of those students. Unlike at any major public firm Zuckerberg still has a majority of voting shares, which means he maintains ultimate control over Meta’s activities. Google was established in 1998, but eventually hired Eric Schmidt who was positioned in the media as the “adult” the company needed. And then there is the chaos unfolding at X (Twitter) that is causing much head-scratching.
So, if getting one’s corporate culture “right” promises peace with society and its regulators and legislators on the one hand and, as historians and business professors argue, promotes the economic success of a firm, where does a high-tech company learn what to do? In the world of IT, sources of positive examples are rare either because they are or more realistically because too many have not been around long enough to have successfully immediately effective corporate norms. A few are obvious: H-P, Microsoft, and increasingly Apple. They are obvious for being around long enough to have succeeded and made errors and corrected these to varying degrees. Old manufacturing firms, of which there are many, are not always seen as relevant case studies, although we have IBM, H-P, and Apple as potential case studies from which to learn. The most senior of these is IBM.

The hard facts about why IBM is the “Mother of All Case Studies” for the IT community is difficult to dispute. First, it was established in 1911 and is still in existence, making it the longest-running IT firm in history. Regardless of how one thinks about IBM, it survived and more often than not thrived, and when adding in the firms that originally made-up IBM, it has done so since the early 1880s.
Second, the empirical evidence increasingly demonstrates—as do my other books about the IT industry’s evolution, use of computing, and of IBM’s market share—that its tabulators dominated the early data processing industry’s supply for a half-century by 90 percent. Depending on which country one looked at, 70 to 80 percent of all mainframes came from IBM in the next 4+ decades, only dipping to about 50-60 percent in the USA due to more IT competition there than anywhere else in the world.
Third, from the 1930s to the late 1980s, IBM also dominated the conversation about the role of data processing (which included more than just about mainframes)—this third point being an important issue I have recently been studying. Attempts to shape public and regulatory opinions about Facebook (Meta), Twitter (X), Amazon, Google, and a myriad collection of Asian firms have bordered on either harmful to the firms (e.g., as is happening with X at the moment) or did nothing to move the needle either in public opinion or in the minds of their customers. My personal observations of the IT world over the past four decades have led me to conclude that the IT community has done a poor job in presenting its various perspectives and value propositions in ways that would enhance their economic and other roles in societies. That is due to mismanaging image creation and dominating the conversation—hence “everyone’s” perspective that would optimize the effectiveness of a firm. This third reason goes far to explain why so much negative press and impressions exist about, for example, social media and online merchants, despite everyone’s belief that they have no choice but to rely on these firms.
All of this is to explain why I wrote Inside IBM: Lessons of a Corporate Culture in Action (Columbia University Press, 2023). I followed frameworks and descriptions of what constituted corporate cultures produced largely by sociologists and business school scholars over the past half-century. I would recommend such a strategy for those looking at, say, IT companies. What these various studies pointed out was that there is a set of common issues to explore. Successful companies define very carefully what their values should be (e.g., at IBM’s “Basic Beliefs) that one can consider, as I phrase it, a form of “corporate theology”—it is there, remains pervasive, and people are held accountable for living it. In IBM’s case this involved providing high levels of customer service, respecting all individuals (that includes customers and citizens at large), and operating in a meritocratic environment where high quality work (“excellence”) was the expected outcome. They implement practices, policies, job descriptions, reward systems, training, and communications that support these values for decades. These are not the program-de-jour or this quarter’s initiative.
The culture experts also point out that such an ethos should attract, engage, and become part of the worldview of customers, regulators, and yes, families of employees. I devote an entire chapter just to how IBM as an institution interacted with families for nearly a century. The evidence made it very clear that this was an organized purposeful exercise, which went far to explain the nature of benefits provided and when (e.g., health insurance, pensions) and sponsored events (e.g., Christmas parties with Santa Claus, summer picnics, employee/spousal trips to Rome, Hawaii, or other resorts).
Keeping other IT companies in mind as possible candidates to study using IBM’s experience as an initial framework for how they might approach the topic, I divided my study into two large categories. The first was both an overview of theories of corporate culture and how they applied in large enterprises accompanied by specific case studies. The latter included discussions of IBM’s corporate theology, how the company functioned on a day-to-day basis (often called by scholars and employees “The IBM Way”), the role of managers in implementing IBM’s culture, how unions could not succeed in the US side of IBM, and employee benefits and relations with families, of course. I could have ended the study at this point because I had explained how IBM had developed and used its corporate culture from roughly the 1910s through the mid-1980s and have clearly documented an effective alignment of culture and strategy that proved successful. However, massive structural and technological changes in the IT world in the 1980s to the present jarred, harmed, and forced changes on IBM altering both in its strategy and culture. I tell that story right up front in an introduction to the historical study because I wanted to also reach current executives in both IBM and all over the industry about what works and does not. In fact, I tell them if all they want is “the answer” to what they should learn from IBM, that introduction is enough, along with perhaps the last chapter if they want their culture to be ubiquitous around the world. As a brief aside, IBM’s culture was universally applied and as Catholic IBM employees often pointed out, it was as consistent in values, rituals, reporting, and activities similarly to the temporal Catholic Church. And just like the Church, IBM implemented its practices essentially the same way. Its Latin was English, its bishops vice presidents, its cardinals, general managers, and so forth.
Then there is the second part of the book, in which we have a partial history of IBM’s material culture. Material culture concerns the cultural and archeological evidence left by a society or organization, in our case such items as products (e.g., computers, boxes with software in them or on floppies and tapes), baseball caps, and coffee mugs with the firm’s name on them, logoed publications, postcards of factories and other buildings, pens and pencils, and myriad other items. Business historians have, to put it bluntly, not studied these ephemera, especially the massive quantity of such objects that have been so popular in the IT industry. Access eBay and type in the name of any IT firm of your choice and you will be surprised, even shocked, at the volume of such material. These logoed items, and the objects used daily in buildings, did not come to be by accident. As a cultural anthropologist or advertising expert will point out, each carries a message, reflects a point of view, and says much about the culture of the firm—THINK signs for over a century (figure 1). But also true, as demonstrated in IBM’s case, they are tied to the purpose of the firm. A PC expert walked around wearing a PC-logoed baseball cap in the 1980s, and in the early 2000s an IBM Consulting Group employee might use a Cross pen with the gray logo of this part of IBM to make it known she was not a “box” peddler for Big Blue. And so, it went.
This book studies a number of types of ephemera to see what they reveal about IBM’s culture. These exposed a great deal normally not discussed in conventional historical monographs. For example, IBMers are considered serious no-nonsense people—an image carefully cultivated for decades in a consistent manner by the corporation that paid enormous dividends (remember “Nobody ever got fired for recommending IBM”?), but IBM had a vast long-standing humorous side to it internally. Thomas Watson, Sr. was presented as a furiously serious leader for over 4 decades while in charge of IBM. Yet he lived in a sales culture where humor and skits were the norm. See Figure 2—yes, he is wearing a Dutch wooden shoe and is smiling; he may well have just participated in a skit in a sales office; other CEOs did too.

Now look at Figure 3, which like so many floated inside the firm, showing a salesman as arrogant, elitist, and dressed quite fashionably. It reflected an attitude found in certain parts of IBM where attire was a humbler affair and where it was believed that the fastest way to build a career in IBM was through sales. Fair? True? It does not matter, because it was a company that employed hundreds of thousands of people and its divisions were like neighborhoods in a city, each with its own personality.

More seriously, IBM wanted the public to see IBM as solid, respectable, professional, and reliable. In the first half of the twentieth century companies all over the world produced postcards to depict such images; IBM was no exception. Watson came from what was considered at the time one of the best run most highly regarded firms in America—NCR—before he commissioned postcards that looked just like the ones he remembered at his prior firm. As IBM expanded and built new buildings, out came more postcards. Some modeled Harvard’s buildings with their trademark cupolas; these were obviously communicating that they were part of a financially solid enterprise. As the firm moved to establish itself as big and elite, a customer or visitor could only get these postcards if visiting such buildings, physically interpreting them. A customer could think, “I am privileged, I was able to be involved in a meeting with the Great IBM.” These were also mementos—think memorializing links—of someone’s connection to IBM (see Figure 4).

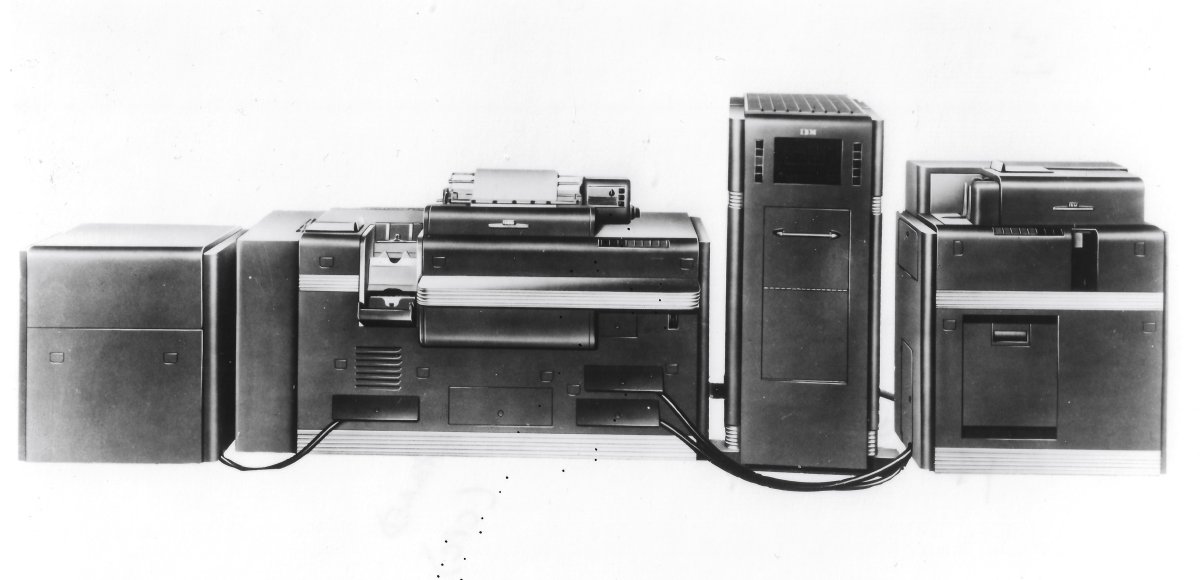
There is a detailed discussion of IBM’s machines complete with some of the most boring product pictures; every IT company produces such images; CBI has an impressive collection of these from many firms that no longer even exist. But these photographs carry messages and reflect corporate attitudes. For example, look at Figure 5 (3.3 p.95). We can agree that it is boring, that it would not win the photograph any prize. However, this 1948 image signaled that IBM thought of this new generation of hardware similarly as it had tabulating equipment for decades, seeing it as a data processing system, not a collection of various products (known colloquially as “boxes”). Note the discrete exposure of cables in front of the machines connecting them all together such that one entered data at one end and out came answers and reports on the other. In real life, those cables would have either been placed behind the machines out of sight or later under those ubiquitous, white-squared floorboards known later as “raised floors.” Dozens of product pictures later, the message was the same: modern, integrated, fashionably designed, big, powerful, and reliable.
IBM also became one of the largest publishers in the world; indeed, there is some dispute about whether it was THE largest one; I take the side of those who think it was the second biggest after the U.S. Government Printing Office. No matter, it was massive, making any collection of academic or trade publishers look tiny in comparison and its publication practices were far more efficient and different than what we experience as authors outside the firm. In the longest chapter in the book, I explain how many publications there were (are); how they were written, published, and distributed; and their purpose. It was not just to persuade someone to buy IBM, or how to use these machines, for the IBM customer engineers how to do that and keep them running or systems engineers how to debug problems. From its earliest days, IBM wanted to dominate what “everyone” worldwide thought about the use of all manner of data processing: customers, opinion makers, academics, executives, politicians, military leaders, employee families, and entire company towns (e.g., where IBM had factories), among others.
This study demonstrated that it had to have a consistent message across all its publications, had to do this for decades, and in sufficient volume to be heard above the din of its competitors and even those publishing in the IEEE, ACM, and trade houses producing books on computing (e.g., Prentice-Hall, Wiley, even MIT). Many of those other outlets published articles and books by IBM authors, again for decades (by me too). But, too, computing was complicated and required a vast body of new information. The chapter starts with a quote of one programmer: “I had perhaps 20 pounds of manuals at my desk to be able to do my job. It was a very paper-intensive time.” An IBM customer engineer called in to fix a machine—and there many thousands of them—came to a data center armed with a fat volume that looked like a Bible with a similar trim size and black leather binding, which they used every working day of their careers. In fact, when they retired, they often kept their personal copy barely suggests the quantity of pages and dense technical text, but the chapter does not spare the reader. Dictionaries of IT terms ran into the many hundreds of pages and had to be constantly updated throughout the second half of the twentieth century, indirectly serving as testimonials to the vast amount of incremental changes that occurred in technology. Pages were replaced in the customer engineering black volumes once or twice weekly with updated ones, done for decades.

Every facet of IBM’s business practices, culture, beliefs, rituals, and events were subjects of company publications. Please read that sentence again. Hundreds of thousands of employees and millions of other people encountered IBM publications and yet no histories of these have been written. Other large enterprises also engaged in extensive publishing—an important finding in this study, because they learned from each other and all needed publications for similar reasons.
Today, Facebook, Apple, and Amazon may have YouTube videos, but IBM and other large firms made training movies, and later videos, beginning in the 1930s; IBM’s archive has a large collection of its own productions. Hollywood’s output was, to be frank about it, tiny in comparison to what collectively such large enterprises did, such as Ford, GM, GE, NCR, and IBM, among others. Their movies and videos projected corporate images integrated into all other message-delivering media for decades and yet these, too, have not been studied. This book about IBM suggests that as with other corporate gray literature, there is much to be learned about other companies and institutions functioning in the world of IT.
An issue that rattles around discussions of corporate culture concerns the level of flexibility in tailoring behavior and operations at some local level, recognizing that business practices in France may or will be different than, say, in Vietnam or New Zealand. What IBM’s experience indicates is that corporate values can essentially be universal, that rituals can be too good for employees, but that processes and operations can be diversified to accommodate local customs and laws. But there are also ground rules for everyone. For instance, American corporations are not allowed by US law to engage in bribery, yet in some countries such practices are common. IBM does not care for that custom; its employees are not allowed to participate in such behavior. On the other hand, for decades IBM had a global no liquor consumption rule most strictly enforced in the United States, but one could find wine in a French IBM cafeteria. Effective corporate cultures can be flexible in how they behave without compromising the core beliefs, image, and ubiquitous practices of the enterprise. That is why, for instance, Apple stores look very much the same around the world, and its products are universal.
Finally, there is the question of how did IBM so standardize its values, behaviors, rituals, practices, managerial behaviors, messages, and expectations of its employees in what ultimately involved some 175 countries. Part of the answer was provided in my earlier publication (IBM: The Rise and Fall and Reinvention of a Global Icon, 2019) where I emphasized lay in the expansion of similar sales, manufacturing, and research facilities around the world, with shared product development, similar sales practices and comprehensive actions to thwart competitors—all traditional business history themes. However, Inside IBM goes a step further, calling the diffusion of a corporate-wide culture the essential strategy for success. Why? How? These are questions currently engaging IT firms and more broadly large national and multinational companies around the world, which brings us back to the point made at the start of this paper that corporations had multiple stakeholders to whom they must serve.
In IBM’s case, several behaviors made universalizing its practices possible. Early on management established a set of beliefs that it refused to alter for decades, maintaining these for so long that eventually, employees could not remember a time or set of values that were different, at least not until late in the twentieth century when much changed. Second, other customers—largely international corporations—encouraged IBM to be able to install products and services on their behalf that were consistent worldwide. IBM was able to do that because it implemented similar practices around the world. That is how, for example, if a large multinational firm wanted an integrated global supply chain it could come to IBM to actually implement it.
Third, generations of managers were trained in the values, culture, and practices of the firm that were consistent, then were called upon to implement and preserve these as a central feature of their work. American management teams exported their ways worldwide and as new generations of employees grew up in that culture outside the US, they exported these to other countries. For example, an IBM manager who grew up in IBM Spain would, upon becoming an executive in Central or South America, would implement—think practice, behave—as earlier in Spain.
Fourth, communications regarding anything IBM was purposefully kept consistent worldwide for decades. Rules, practices, and guidelines were communicated and kept (or changed) in a consistent manner worldwide to the degree that local custom made possible. Much commonality proved possible to maintain in most countries and whenever not so, the firm was prepared to evacuate from a national market for as long as required (e.g., India, South Africa, and recently Russia).
While historians of the IT world are strongly attracted to its technology, as is occurring to the Internet’s technological evolution, emergence, and diffusion, so too there is growing interest in the less precisely defined issues of managerial practices, sociology of institutions, role in society, and so forth. Corporate culture has long been seen in business managerial studies as crucial and it seems today that so many CEOs are declaring that to be so. IBM has much to teach today’s generation of scholars and executives how that was done effectively, even if occasionally poorly.
Finally, I should point out what is missing from my research—so far—and from this article: the role of minorities in multiple countries, and specifically in the U.S. side of the business. Women in IBM, in particular, are insufficiently studied, yet they played roles common to many corporations in each decade and, as in other firms, slowly expanded their positions broadly and upwardly in the company’s managerial ranks. But that is a story that requires a far deeper dive than I have been able to perform—again so far—in this article or in my earlier studies.
Bibliography
Cortada, James W. (2018). Change and Continuity at IBM: Key Themes in Histories of IBM. Business History Review 92(1), 117-148.
Cortada, James W. (2019). IBM: The Rise and Fall and Reinvention of a Global Icon. (MIT Press, 2019).
Cortada, James W. (2023). Inside IBM: Lessons of a Corporate Culture in Action. (Columbia University Press).
Denison, Daniel R. (1997). Corporate Culture and Organizational Effectiveness. (Denison Consulting).
Hofstede, Geert. (1991). Cultures and Organizations: Software of the Mind. (McGraw Hill).
Kotter, John P. and James I. Haskett. (1992). Corporate Culture and Performance. (Free Press).
Schein, Edgar H. (1985, 1989). Organizational Culture and Leadership. (Jossey-Bass).
James W. Cortada (February 2024). “High Tech Corporate Culture: IBM’s Experience and Lessons.” Interfaces: Essays and Reviews on Computing and Culture Vol. 5, Charles Babbage Institute, University of Minnesota, 11-22.
About the author: James W. Cortada is a Senior Research Fellow at the Charles Babbage Institute, University of Minnesota—Twin Cities. He conducts research on the history of information and computing in business. He is the author of IBM: The Rise and Fall and Reinvention of a Global Icon (MIT Press, 2019). He is currently conducting research on the role of information ecosystems and infrastructures.
Turing Award winner Geoffrey Hinton and former Google chief executive Eric Schmidt are only two among many people who have recently voiced their concerns about an existential threat from AI. [See, for example, Brown 2023; Roush 2023.] But what does it mean for a technology or, for that matter, something else such as a natural disaster, a war, or a political ideology to be an existential threat? An existential threat must be directed at a particular target audience that is threatened and to a particular aspect of their life that is at risk. We only care, as a society, about existential threats if the target audience is dear to us and the item at risk is significant. The consequences of an existential threat may be biological, psychological, economic, organizational, or cultural. Thus, multiple academic fields provide a perspective on existential threat.
In this article, our goal is not to argue about whether AI is or is not an existential threat—or even to describe who AI threatens and what elements are at stake. Instead, our focus here is to provide the reader with a multidisciplinary toolset to consider the concept of existential threat. To achieve this, we introduce the reader to four organizations that study this topic, along with the relevant literature by individual scholars. It is beyond the scope here to apply these various perspectives on existential threat to developments in AI.

Research Institutes
We begin by profiling four research institutes: the Käte Hamburger Center for Apocalytic and Post-Apocalytic Studies, the University of Cambridge Centre for the Study of Existential Risk, the University of Oxford Future of Humanity Institute, and the Stanford (University) Existential Risks Initiative. (A much longer list of relevant organizations can be found on the Stanford Existential Risks Initiative webpage: https://seri.stanford.edu/resources.) [Editors' note: links to all websites mentioned are in the Bibliography]
Käte Hamburger Center for Apocalyptic and Post-Apocalyptic Studies
The Käte Hamburger Center for Apocalytic and Post-Apocalytic Studies (CAPAS) at Heidelberg University, which began operation in 2021, is one of 14 research centers sponsored by the German Federal Ministry of Education and Research. We spend more time on this center because it is probably the least familiar of these centers to the American reader. The goal of CAPAS is to study the “effects of catastrophes and end-time scenarios on societies, individuals, and environments”. CAPAS expands on this goal on the About page of its website:
By focusing on social mechanisms and coping strategies of crises through the prism of the apocalypse, CAPAS provides applied knowledge about successful and failed responses to existential threats and their consequences. On this basis, the Centre contributes to topical debates on potential ecological and social breakdown. CAPAS thus sees itself as a platform for reflection on perceived doom that helps to strengthen societal and political resilience to end-of-life scenarios of all kinds and to anticipate social risks.
In its first years, the center has focused on a strength of its home university in the study of South/East Asia and the Americas by examining “the apocalyptic imaginary that frames the COVID-19 pandemic”. This interest goes beyond this crisis to examine other kinds of apocalyptic events such as world environmental crises and digital control over human thought and action. The current lecture series, for example, includes topics related to the apocalypse and post-apocalyptic thinking in various ways, concerning smart cities, Orientalism and Western decline, desert architectures, raising children, psychanalysis, and concepts of time.
The Center employs a transdisciplinary approach that includes the humanities as well as the social and natural sciences. As the Center explains on their Our Premises page: “Thus, in addition to empirically based natural and social sciences, CAPAS uses the potential of interpretive humanistic approaches to comprehensively reconstruct and analyse conceptions and experiences of apocalypses and post-apocalyptic worlds. Thereby, the humanities allow us to investigate and challenge possible future scenarios that are beyond the predictive capacity of purely empirical sciences.”
The Center invites ten fellows from around the world each year. As outlined on the Fellows page, the Fellow’s research at the Center must relate to: “our three research areas (A) the apocalyptic and postapocalyptic imaginary (ideas, images, discourses), (B) historical events that were perceived or framed as (post-)apocalyptic experiences, and (C) current, empirically observable developments that could bring about the end of the world as we know it and its aftermath scenarios.”
In addition to the fellowship program, the Center offers public lectures, a bi-weekly newsletter, and a quarterly magazine. The directors of the Center are Robert Folger, a professor of Romance Literature, and Thomas Meier, an archeologist who studies pre- and early history, both professors work at Heidelberg University.

Stanford Existential Risks Initiative
In 2019 Stanford University created the Stanford Existential Risks Initiative to engage the student body, faculty, and outside community in the study and mitigation of existential risks, which they define as:
risks that could cause the collapse of human civilization or even the extinction of the human species. Prominent examples of human-driven global catastrophic risks include 1) nuclear winter, 2) an infectious disease pandemic engineered by malevolent actors using synthetic biology, 3) catastrophic accidents/misuse involving AI, and 4) climate change and/or environmental degradation creating biological and physical conditions that thriving human civilizations would not survive.
The initiative teaches a freshman course on Preventing Human Extinction, offers a postdoctoral fellowship in the areas of advanced artificial intelligence, biological risks, nuclear risks, and extreme climate change; a summer undergraduate research fellowship; an annual conference (2023 conference proceedings); a speaker series; a discussion group; and an online Cascading Risks survey open to adults.
The initiative is run by Paul Edwards, a professor of science, technology, and society who is well known in the history of the computing community for his monographs The Closed World and A Vast Machine [Edwards 1997, 2010], and Steve Luby, a professor of medical and health policy; together with the student organizer, Michael Byun, who is an undergraduate computer science major.
Cambridge Centre for the Study of Existential Risk (CSER)
In 2012, the University of Cambridge began to reallocate resources to form an interdisciplinary research center to study how to reduce existential risks associated with emerging technologies. The first postdocs were appointed in 2015. The co-founders were the Astronomer Royal and professor at Cambridge of Cosmology and Astrophysics Martin Rees, co-founder of Skype and Kazaa Jaan Tallinn, and Bertrand Russell Professor of Philosophy at Cambridge Huw Price. The director is Matthew Connelly, professor of international and global history at Columbia University. The Centre’s goals are:
- To study extreme risks associated with emerging and future technological advances;
- To develop a methodological toolkit to aid in the perception and analysis of these risks;
- To examine issues surrounding the perception and analysis of these risks in the scientific community, the public and civil society, and develop strategies for working fruitfully with industry and policymakers on avoiding risks while making progress on beneficial technologies;
- to foster a reflective, interdisciplinary, global community of academics, technologists, and policymakers; and
- to focus in particular on risks that are (a) globally catastrophic in scale (b) plausible but poorly characterized or understood (c) capable of being studied rigorously or addressed (d) clearly play to CSER’s strengths (interdisciplinarity, convening power, policy/industry links) (e) require long-range thinking. In other words, extreme risks are where we can expect to achieve something.
The Centre is working to have several impacts: to influence policy in various national and international governmental bodies; to build, through “collaborations, media appearances, reports, papers, books, workshops – and especially through our Cambridge Conference on Catastrophic Risk” a community of people from various walks of life to help reduce existential risk; to convene experts from academic, industry, and government to share cutting edge knowledge about relevant topics such as biological weapons; and to build an academic field concerning long-term AI safety.
In 2023, CSER was made a part of Cambridge’s newly created Institute for Technology and Humanity, (ITH) which is dedicated to research and teaching “that investigates and shapes technological transformations and the opportunities and challenges they pose for our societies, our environment and our world.” This organizational structure may lead to a collaboration with two other centres that are now part of ITH: Leverhulme Centre for the Future of Intelligence and Centre for Human-inspired AI.
Oxford Future of Humanity Institute
In 2005, University of Oxford philosopher Nick Bostrom created the Future of Humanities Institute as a part of a larger new initiative called the Oxford Martin School. Much of the focus has been on the existential risk of both the natural and the human-made varieties, studied using the tools of mathematics, philosophy, and the social sciences. For example, Bostrom and Milan Circovic published an edited volume on Global Catastrophic Risks [Bostrom and Circovic 2008], and between 2008 and 2010, the Institute hosted the Global Catastrophic Risks Conference. For more than a decade, the Institute has been concerned about AI, e.g., with the publication of Bostrom’s Superintelligence: Paths, Dangers, Strategies [Bostrom 2014]. Currently, the Institute has research groups which are working in the following areas: macrostrategy [the impact of present-day activities on the long-term fate of humanity], governance of AI, AI safety, biosecurity, and digital minds.
The Institute, and Bostrom in particular, has been an influential voice in public discussions of existential risk, for example in giving policy advice to the World Economic Forum and the World Health Organization. Bostrom and colleagues at the Institute have been very active in their publication, with academic, policy, and general public audiences in mind. (See the extensive list of publications on the Future of Humanity Institute Publications page and the list of Technical Publications.)
Much of the Institute’s work is done in collaboration with other organizations, including the Centre for Effective Altruism, with which they share space, and with their parent organization, the Oxford Martin School. Other collaborators have included, from the early days, DeepMind—and more recently, the Partnership on AI (which includes DeepMind, OpenAI, Facebook, Amazon, IBM Microsoft, Sony, Human Rights Watch, UNICEF, and others).

Academic Literature on Existential Threat
While there have been many historical studies of individual catastrophes, from the fall of the Roman Empire to the Titanic to COVID-19, there are a few books that provide us with a historical overview of various kinds of existential threats. Some examples include a book by the award-winning television reporter and producer John Withington, Disaster! A History of Earthquakes, Floods, Plagues, and Other Catastrophes [Withington 2012], which gives a long history since antiquity; or, with a focus on catastrophes in the post-WW2 era, see the book by the Marxist professor of European studies from Kings College, London, Alex Callinicos, entitled The New Age of Catastrophe and by history professor at University of Massachusetts Boston, Lisa Vox, Existential Threats: American Apocalyptic Beliefs in the Technological Era. [Withington 2012; Callinicos 2023; Vox 2017] Also see a useful article by Thomas Moynihan on the intellectual history of existential risk and human extinction. [Moynihan 2020]
Harvard Business School professor Clayton Christiansen published a best seller in the business and management literature, entitled The Innovator’s Dilemma: When New Technologies Cause Great Firms to Fail. [Christiansen 1997] While many technologies engender new product development, Christiansen points out that some innovations can be “disruptive”—causing poorer product performance and possibly even the failure of individual products, companies, or industries. For example, small Japanese motorcycles were disruptive to the typical large motorcycles sold in America by BMW and Harley Davidson, while health maintenance organizations were disruptive to traditional health insurers. Or more pertinent here, transistors and microcomputers were disruptive in the computer industry. This led to extensive business and management literature on the issue of disruptive technologies and their threat to products, firms, and industries—extending and refining Christiansen’s model, finding “solutions” to it, and applying it in various contexts.
Nick Bostrom, the founder of the Oxford Institute mentioned above, is the foremost scholar from academic philosophy studying human-created existential threats, such as might occur with AI, nanotechnology, or synthetic biology. He has written on such topics as comparison between human-created disasters and natural disasters, the possibilities of superintelligence through AI and ways of categorizing superintelligence, and policy approaches to address existential threats. While his work is widely cited and praised, his theories have some critics including the philosophers Daniel Dennett and Oren Etzioni; and he has become controversial for both racist emails he has sent and his advocacy of the life philosophy of effective altruism, which some women believe create a culture of sexual harassment and abuse. [See Bilyard 2023; Alter 2023] In addition to Bostrom’s two books cited above, also see his Anthropic Bias and Human Enhancement. [Bostrum 2002; Savulescu and Bostrom 2009]
For some time, social psychologists have been interested in the psychology of risk, and there has been a significant body of empirical research on the topic. These scholars are interested in how people perceive and analyze risk, how they determine the amount of risk associated with a particular hazard, how they behave towards and make decisions about risk, how individuals communicate with others about risk, behavior towards and attitudes about accidents, how risks are treated by society, and how risk is connected to one’s identity. [See, for example, Breakwell 2014.] Breakwell writes:
Since the first edition of The Psychology of Risk was published in 2007, the world has changed. The world is always changing but the years since 2007 have seen enormous macro-economic and socio-political changes globally—the chaos in the world banking system and the financial crisis and recessions that it presaged; the Arab Spring and the revolutionary shifts in power in the Middle East with rippled consequences around the world; the development of ever-more sophisticated cyber-terrorism that can strike the private individual or the nation-state with equal ease. …The question then arises: amidst these changes in the face of hazard, do the psychological models earlier built to explain human reactions to risk still apply? Do they need to be modified? [Breakwell 2014, p. xii.]
With risk taken to the extreme of existential risk, there is additional scholarship in this area in recent times. [See, for example: Currie 2019; Jebari 2015; Klisanan 2023; Kreutzer 2021; Lawn et al. 2022; Ord 2020; Schubert, Caviola, and Faber 2019; Schuster and Woods 2021; Syropoulos et al. 2023a, 2023b, 2023c]
Sometimes, when people claim that AI or some other event is an existential threat, their claim is simply an unexplored rhetorical strategy to cry wolf. Many of these utterances are unaccompanied by a careful examination of the exact nature of the threat or of the particular consequences that might ensue. The readings pointed to here provide the reader with a variety of approaches they might use to examine more thoroughly these potential threats and their potential consequences—examining, for example, both the various kinds of existential threats that may arise and how these threats compare to one another; and various lenses for examining the technical, political, economic, and cultural consequences they might have.
Thanks to my colleagues Jeff Yost and Jim Cortada for comments on an earlier draft.
Bibliography
Alter, Charlotte. 2023. Effective Altruism Promises to Do Good Better. These Women Say It has a Toxic Culture of Sexual Harassment and Abuse, Time (February 3), https://time.com/6252617/effective-altruism-sexual-harassment/ (accessed 6 December).
Bilyard, Dylan. 2023. Investigation Launched into Oxford Don’s Racist Email, The Oxford Blue (15 January).
Bostrom, Nick. 2002. Anthropic Bias: Observation Selection Effects in Science and Philosophy (Routledge).
Bostrom, Nick. 2014. Superintelligence: Paths, Dangers, Strategies (Oxford University Press).
Bostrom, Nick and Milan Circovic, eds. 2008. Global Catastrophic Risks (Oxford University Press).
Breakwell, Glynis M. 2014. The Psychology of Risk (2nd ed., Cambridge University Press).
Brown, Sara. 2023. Why Neural Net Pioneer Geoffrey Hinton is Sounding the Alarm on AI, MIT Management (23 May), https://mitsloan.mit.edu/ideas-made-to-matter/why-neural-net-pioneer-geoffrey-hinton-sounding-alarm-ai#:~:text=Hinton%20said%20he%20long%20thought,things%20humans%20can%27t%20do (accessed 6 December 2023).
Callinicos, Alex. 2023. The New Age of Catastrophe (Polity).
Cambridge Centre for the Study of Existential Risk (CSER). Our Mission.
Cambridge Centre for the Study of Existential Risk (CSER). About us.
Christiansen, Clayton. 1997. The Innovator’s Dilemma: When New Technologies Cause Great Firms to Fail (Harvard Business School Press).
Currie, Adrian. 2019. Existential Risk, Creativity & Well-adapted Science, Studies in History and Philosophy of Science Part A76: 39-48.
Edwards, Paul N. 1997. The Closed World: Computers and the Politics of Discourse in Cold War America (MIT Press).
Edwards, Paul N. 2010. A Vast Machine: Computer Models, Climate Data, and the Politics of Global Warming (MIT Press).
Jebari, Karim. 2015. Existential Risks: Exploring a Robust Risk Reduction Strategy." Science and Engineering Ethics 21, no. 3: 541-554.
Käte Hamburger Centre for Apocalyptic and Post-Apocalyptic Studies (CAPAS). About Us.
Käte Hamburger Centre for Apocalyptic and Post-Apocalyptic Studies (CAPAS). Fellowships at CAPAS.
Käte Hamburger Centre for Apocalyptic and Post-Apocalyptic Studies (CAPAS). Our Premises.
Käte Hamburger Centre for Apocalyptic and Post-Apocalyptic Studies (CAPAS). Research.
Klisanin, Dana. 2023. Existential Risk: From Resilience to Antifragility." Intersections, Reinforcements, Cascades: 50-59.
Kreutzer, Philipp Jonas. 2021. Would You Think We Are Doomed Because of Climate Change?, School of Economics and Management, Lund University, https://lup.lub.lu.se/luur/download?func=downloadFile&recordOId=9058790&fileOId=9058792 (accessed 6 December 2023).
Ladden-Hall, Dan (12 January 2023). "Top Oxford Philosopher Nick Bostrom Admits Writing 'Disgusting' N-Word Mass Email". The Daily Beast. Retrieved 12 January 2023.
Lawn, Erin CR, Luke D. Smillie, Luiza B. Pacheco, and Simon M. Laham. 2022. From Ordinary to Extraordinary: A Roadmap for Studying the Psychology of Moral Exceptionality." Current Opinion in Psychology 43: 329-334.
Moynihan, Thomas. 2020. Existential Risk and Human Extinction: An Intellectual History, Futures 116.
Ord, Toby. 2020. The Precipice: Existential Risk and the Future of Humanity. Hachette Books, 2020.
Oxford Future of Humanity Institute. About FHI.
Oxford Future of Humanity Institute. Publications.
Oxford Future of Humanity Institute. Technical Reports.
Roush, Ty. 2023. Ex-Google CEO Warns Current AI Guardrails ‘Aren’t Enough’—Likened Development to Nuclear Weapons, Forbes (November 28), https://www.forbes.com/sites/tylerroush/2023/11/28/ex-google-ceo-warns-current-ai-guardrails-arent-enough-likened-development-to-nuclear-weapons/?sh=e075dbcf84be (accessed 6 December 2023).
Savulescu, Julian and Nick Bostrom, eds. 2009. Human Enhancement (Oxford University Press).
Schubert, Stefan, Lucius Caviola, and Nadira S. Faber. 2019. The Psychology of Existential Risk: Moral Judgments about Human Extinction." Scientific Reports 9, no. 1: 15100.
Schuster, Joshua, and Derek Woods. 2021. Calamity Theory: Three critiques of Existential Risk (University of Minnesota Press).
Stanford Existential Risks Initiative. Resources.
Stanford Existential Risks Initiative. Intersections, Reinforcements, Cascades: Proceedings of the 2023 Stanford Existential Risks Conference.
Syropoulos, Stylianos, Kyle Fiore Law, Gordon Kraft-Todd, and Liane Young. 2023a. The Longtermism Beliefs Scale: Measuring Lay Beliefs for Protecting Humanity’s Longterm Future.
Syropoulos, Stylianos, Kyle Fiore Law, Matthew Coleman, and Liane Young. 2023b. A Future Beyond Ourselves: Can Self-oriented Prospection Bridge Responsibility for Future Generations?
Syropoulos, Stylianos, Kyle Fiore Law, and Liane Young. 2023c. Caring for Future Generations: Longtermism and the Moral Standing of Future People.
Vox, Lisa. 2017. Existential Threats: American Apocalyptic Beliefs in the Technological Era (University of Pennsylvania Press).
Withington, John. 2012. Disaster! A History of Earthquakes, Floods, Plagues, and Other Catastrophes (Skyhorse).
William Aspray (January 2024). “Is AI an Existential Threat? Let’s First Understand What an Existential Threat Is.” Interfaces: Essays and Reviews on Computing and Culture Vol. 5, Charles Babbage Institute, University of Minnesota, 1-10.
About the author: William Aspray is Senior Research Fellow at CBI. He formerly taught in the information schools at Indiana, Texas, and Colorado; and served as a senior administrator at CBI, the IEEE History Center, and Computing Research Association. He is the co-editor with Melissa Ocepek of Deciding Where to Live (Rowman & Littlefield, 2021). Other recent publications include Computing and the National Science Foundation (ACM Books, 2019, with Peter Freeman and W. Richards Adrion); and Fake News Nation and From Urban Legends to Political Fact-Checking (both with James Cortada in 2019, published by Rowman & Littlefield and Springer, respectively).
This paper expands on a dated but relevant concept from science and technology studies centered on gender inequality named cyberfeminism. Cyberfeminism is a concept, approach, or movement from the 1990s that sought to increase and solidify women’s representation in science and technology by having them embrace science and technology in their ways. Cyberfeminism peaked in the 1990s but faded in the aughts with Y2K and the dot com boom (Evans, 2016; Paasonen, 2011). The Multimedia Encyclopedia of Women in Today's World entry for cyberfeminism states,
Cyberfeminism refers to a philosophy and community that began in the 1990s along with Third-Wave feminism. Cyberfeminism is dedicated to the intersections of feminism and technology, specifically the Internet. Drawing on postmodern theories of identity and gender, cyberfeminism is a philosophical movement that finds itself at odds with labels and attempts to limit and categorize it as a definitive genre or philosophical set of practices. (Harlow, 2013, p.429)
This definition hints at the vagueness and malleability of the term, which was the intention of founding theorists and practitioners. It also gets at the nuance of the term. The usage of its prefix, cyber, fell out of favor as the Internet and Web became standardized and its suffix, feminism, is open to various interpretations. Cyberfeminisms, is my preferred usage because it implies multiplicity instead of singularity, which is needed when examining the intersections of technology and inequalities.
In this paper, I use cyberfeminism (without the s) only for consistency and historical context. However, as the title of this paper suggests, my preferred term is cyberfeminism(s). I define cyberfeminism(s) as a malleable approach, techno-philosophy, community, and method that aims to address gender inequalities in science and technology but can also be used to address other inequalities that intersect gender, like race, ethnicity, sexual identity, and ability through collaboration, strategy, and creativity. This paper will provide a historical overview of cyberfeminism by surveying its geographical origins, analyzing its critiques, and reviewing its strategies and themes. The scope of cyberfeminism in this paper is limited to self-identified women and girls as early cyberfeminism centered mainly on this group, although there were many debates and discussions against the gender binary due to the fluidity of sexuality and gender online (Chatterjee, 2002; Daniels, 2009; Haraway, 1985; Oksala, 1998; Plant, 1997).
Cyberfeminism: The Beginning
Cyberfeminism has no one definition, so what it is could be defined by anyone who finds themselves fascinated by aspects of it. The malleability of the definition was an intentional choice by early cyberfeminists to appeal to different groups of women (Solfrank, 2017). It gained traction in the 1990s following the increase in usage of the Internet and Web. Both technologies were often conflated as one, despite being separate things (hardware vs. software), as the use of the term “cyberspace” implied they were one entity. With more people outside the government using the Internet and the Web, different groups and cultures were sorting out how to use cyberspace (hereafter meant as a combination of the Internet and Web). Cyberfeminism is closely associated with Donna Haraway, even though she has never self-identified as one. Her influential work, Cyborg Manifesto (Haraway, 1985), can be seen in cyberfeminism’s Australian, European, and North American origins.
Australia: VNS Matrix
VNS Matrix was a four-woman art collective based in Adelaide, Australia, and is often cited for visually conceptualizing what cyberfeminism could be (Evans, 2014; Scott, 2016; Solfrank, 2017). The members included Josephine Starrs, Julianne Pierce, Francesca da Rimini, and Virginia Barratt (Evans, 2014). These women called themselves “power hackers and machine lovers” and declared that they were the “virus of the new world disorder” and “terminators of the moral codes” (Scott, 2016, para.4; Evans, 2014, para. 2). They took a multimedia approach by making cyberfeministic art through computer games, texts, billboards, and video installations (Evans, 2014). Their most well-known “gyne-canonical” text, where many claim the term “cyberfeminism” was named, was their 1991 Cyberfeminist Manifesto for the 21st Century (Evans, 2014; Scott, 2016; Solfrank, 2017; VNS Matrix, n.d.-a.) The manifesto starts with the following,
we are the modern
cunt positive anti reason
unbounded unleashed unforgiving (VNS Matrix, n.d.-a).
The four members wrote it during a stream-of-consciousness writing session, and they noted that it was written in a way that highlighted the conditions of early network culture and cyberspace (Net Art Anthology, n.d.). The session was meant to be “collaborative, plagiaristic, possibly drug-fueled, and pornographic” (Net Art Anthology, n.d., para.2). They used elements from their manifesto to craft an 18-foot billboard with 17 lines of text in Sydney, Australia. It featured half-naked women merged with animal parts and random animated images of DNA with a blue color scheme, as seen in Figure 1 (Evans, 2016; VNS Matrix, n.d.-c). Both the manifesto and images of the billboard were shared through fax, mail, poster, other billboards, and chat rooms, “adopting the techniques of propaganda as an art practice” (Net Art Anthology, n.d., para. 2).

Another popular work from VNS Matrix was their 1995 computer game, All New Gen, as seen in Figure 2. The game was initially titled Game Girl, an intentional play on words to the Game Boy console (VNS Matrix, n.d.-b). This satirical game disrupted gender and technology stereotypes by having the heroines of the game be “cybersluts,” and “anarcho cyber-terrorists” fighting against the phallic power of “Big Daddy Mainframe” with “G-slime—goo shot from weaponized clitorises” (Scott, 2016, para. 6). The game is a great example of the “in your face” sexuality that accompanies cyberfeminism. I argue that VNS Matrix was the most sexual or sexually charged originator of cyberfeminism. They wanted to subvert and defeat stereotypical, misogynistic, and pornographic representations of women by using images and concepts of them owning their sexuality, prowess, and bodies online (Evans, 2014). It made one think beyond the images and was a great way to generate conversations about women online.

Europe: United Kingdom
British philosopher and cultural theorist Sadie Plant was the other individual associated with coining the term cyberfeminism. She is credited with crafting early academic theory on cyberfeminism but received much criticism from cyberfeminist practitioners who focused on art and activism (Paasonen, 2011). Plant (1997) wrote about forgotten women scientists and inventors and highlighted their downplayed historical achievements in her most well-known work, Zeros and Ones: Digital Women and the New Technoculture. British mathematician Ada Lovelace is one of the women inventors she highlights. Lovelace made significant under-appreciated contributions to the computer industry and created the first-ever algorithm in 1843 (Scott, 2016). Charles Babbage, considered the father of the computer, used many of her notes in his work, but she never received the credit she deserved. Her work was overshadowed by her gambling, drinking, and contentious parentage (her father was poet Lord Byron) (Plant, 1997). Plant claims society treats women like the zeros in binary digits and men like the ones (Plant, 1997, pp.34-35). “Woman functions as a hole, a gap, a space, a nothing - that is nothing the same, identical, identifiable … a fault, flaw and lack of absence, outside the system of representations and autorepresenations” (Plant, 1997, p.35) She claims that despite it taking two to make a binary, if a woman is zero, and a man is one, combined they will always make another one, so when can the woman (zero) stand out (Plant, 1997, p.35). Women’s role in science, technology, engineering, and mathematics (STEM) has been precoded not to be important or overshadow the phallic power of the number one in Western reality (Plant, 1997; Sollfrank, 2017). The central argument of her book is that despite male oppression and historical revision, women have always been involved in STEM and had major achievements that many are unaware of. However, some cyberfeminists felt that Plant receives too much credit for coining the term cyberfeminism, despite pulling some of the content for her book directly from VNS Matrix (Paasonen, 2011). Others thought her work was too theoretical and focused too much on comparing women’s history in STEM to men's (Paasonen, 2011). The historical aspects of her book are both her strength and weakness because as thorough as Plant’s review of Western civilization’s disregard for women scientists and inventors is – it does not encompass everything that makes up cyberfeminism. Throughout the book, Plant acknowledges the underappreciated achievements of women in science and technology, but she does not offer any solutions or interventions that align with the liberation of women through science and technology or combating online misogyny.
Europe: Germany
Around 1997, enough women identified as cyberfeminists, that a Berlin-based feminist collective intentionally named the Old Boys Network (OBN) hosted the First Cyberfeminist International held in Kassel, Germany (Solfrank, 2017). The promotional materials for the conference were very “cheeky” and highlighted that it was an event about technology for and about women. Figure 5 shows a “cheeky” flier promoting the conference that used a giant period and a parenthesis to resemble a breast and a nipple with conference logistics at the bottom in a smaller font. 38 women from 12 countries came together to discuss cyberfeminism in person (Scott, 2016). At this conference, they attempted to define cyberfeminism but struggled because of their non-hierarchal and open approach when planning the conference. However, one of the founders of the OBN, Cornelia Sollfrank, described the conference as a “euphoric atmosphere” (Solfrank, 2017, para. 20) where everyone was able to contribute something. These contributions can be seen in one of the results of the conference. Since they were struggling to define cyberfeminism, they decided to define what it was not, which they did through a “provocative anti-manifesto” titled 100 Anti-Theses of Cyberfeminism (Solfrank, 2017; Paasonen, 2011). The title may be a nod to German priest Martin Luther’s provocative Ninety-five Theses against the Catholic Church. Their anti-manifesto featured multiple languages and had humorous and serious suggestions. Some anti-theses included “cyberfeminism is not a fashion statement, cyberfeminism is not an ideology, cyberfeminism is not a fragrance” (Wilding, n.d., p. 10). Their ironic strategy to go a different route and leave the term undefined has been noted as why it never entered the mainstream and had such a short lifespan. “This performative rejection of the political need to define our commonalities indicated a new beginning that later has often been misread as lack of political rigor” (Sollfrank, 2017, para.20). It was both a strength and a weakness to conceptualize cyberfeminism in such a laissez-faire manner.


North America: USA and (Canada)
The North American contributions to cyberfeminism were much more critical of the movements and approaches in other geographies and precipitated its eventual “end.” Influential figures from the U.S. included artist Faith Wilding and scholars Maria Fernandez and Anna Everett. The most well-known Canadian cyberfeminist was the artist, Nancy Patterson. Some in the cyberfeminist community believe that Patterson never received the same acknowledgment as VNS Matrix and Sadie Plant for coining the term cyberfeminism, which she named in her influential 1992 new media art history paper, Cyberfeminism (Paasonen, 2011). In that paper, Patterson focused on gender diversity and cultural subversion in new technologies (Langill, 2009). She emphasized how new technologies can reinforce stereotypes but can also empower marginalized groups to use those technologies to counter those stereotypes (Paasonen, 2011). One can see contemporary examples of Patterson’s argument, particularly in social media campaigns geared towards increasing non-superficial representation and awareness for disadvantaged groups, like in the recent #MeToo and #SayHerName campaigns.
Artist Faith Wilding was a participant-informant at the First Cyberfeminist International and left the conference with many thoughts concerning the privilege of the participants and their ideas (Everett, 2004; Wilding, 1998). She shared these thoughts in a 1998 essay titled, “Where is the Feminism in Cyberfeminism?” for The Feminist eZine (Wilding, 1998). She noticed that some participants hesitated to learn or build on work from the previous waves of feminism despite the cyberfeminist community already using some of their strategies and methods (Wilding, 1998). It included “strategic separatism (women-only lists, self-help groups, chat groups, networks, and woman-to-woman technological training) [and the] creation of new images of women on the Net to counter rampant sexist stereotyping (feminist avatars, cyborgs, genderfusion)” (Wilding, 1998, p.11). The apprehension between learning and building from previous feminist struggles but being eager to work with new technologies was a strange disconnect to Wilding (1998) because combining both was essential to reducing disparities in cyberspace. The historical and cultural context that came with First and Second-wave feminism was downplayed, according to Wilding (1998), as she reported that some even felt uncomfortable identifying as feminists without using the prefix cyber (Paasonen, 2011; Wilding, 1998).
She also cautioned her peers about the rebellious “cybergrrl-ism” aspect of cyberfeminism, which she claimed, “generally seems to subscribe to a certain amount of net utopianism--an "anything you wanna be and do in cyberspace is cool" attitude” (Wilding, 1998, p.8). The “riot grrl” influence from music (punk) and art (zines) seeped into cyberfeminist practice. However, she felt cybergrrl-ism was too focused on the performance and appearance of being a woman or girl in cyberspace and not enough on getting more women and girls in cyberspace (Wilding, 1998). She stated, “being bad grrls on the Internet is not by itself going to challenge the status quo” (Wilding, 1998, p.9). Borrowing language and ideas from feminists that came before her, Wilding (1998) states, “the personal computer is the political computer” to remind those interested in cyberfeminism that technology is inherently political. She remained wary of cyberfeminism without political theory and believed its strength came from the combination of political theory, art, and popular culture.
Wilding (1998) also called out cyberfeminism’s lack of intersectionality and involvement of women in the Global South. “Cyberfeminism presents itself as inclusive, but the cyberfeminist writings assume an educated, white, upper-middle-class, English speaking, culturally sophisticated readership” (Scott, 2016, para.14). White people with computers were overrepresented in early cyberspace, so Wilding wanted cyberfeminism to work more with and for marginalized groups. Wilding attempted to do more with that in real life to address the lack of intersectionality in cyberfeminism through her art and writing. She founded subRosa, a feminist art collective critical of the “intersections of information and biotechnologies on women’s bodies, lives and works” through workshops and performances that still exist today (subRosa, 2013, para. 1; Scott, 2016). In addition, she wrote texts with post-colonial media scholar Maria Fernandez. One of those works includes the post-Y2K text, Domain Errors!: Cyberfeminist Practices, which was the first cyberfeminist text to address intersectionality and post-colonialism (Fernandez et al., 2002).
Cyberwomanism
A scholar not included in early cyberfeminist history but should be is media and film scholar, Anna Everett. Oddly, the sole Black woman who did early scholarly work for cyberfeminism is not acknowledged in its history despite it being a movement geared at increasing representation (Wilding, 1998). Everett (2004) conducted ethnographic research on how Black women utilized cyberfeminism but named it cyberwomanism, an ode to writer Alice Walker’s conceptualization of Black feminism. Everett (2004) conducted a comparative analysis of 1997’s First Cyberfeminist International, and the 1997 Million Women’s March held in Philadelphia, which Black women organized through cyberspace. The event was similar to the Million Man’s March of 1995 but centered on the well-being and self-determination of Black women. The Million Women’s March had about 750,000 thousand participants compared to the 38 attendants at the Cyberfeminist International, but this incredible feat has still not been acknowledged by the community (Everett, 2004, p.1282). Everett notes how Black women used cyberspace to organize for the March despite not all attendees having a computer or internet access. They bypassed this by having folks who worked with computers and the Internet print pages from their website for those who did not have access to either (Everett, 2004). This was done at the peak of the digital divide, so it should be noted in cyberfeminist history (Everett, 2004, p.1282). She mentions that the cyberfeminists in Germany looked at cyberspace as the primary problem. In contrast, the “cyberwomanists” in the US considered it the primary solution (Everett, 2004, p.1280).
Regardless, both approaches were notable achievements for women in cyberspace and showed how non-white women could use cyberspace to advocate for themselves. For marginalized populations, cyberspace can be an open or closed space. Daniels (2009), Gajjala & Oh (2012), Russell (2020), and Wilding (1998) note the critiques of cyberfeminism when it comes to intersectionality, especially regarding race, gender, and sexuality. In her article, Rethinking Cyberfeminism(s): Race, Gender, and Embodiment, sociologist Jessie Daniels (2009) argues that self-identified girls and women engage in practices with internet technologies to transform their material and corporeal lives in complex ways that both resist and reinforce hierarchies of gender and race by using case studies such as pro-ana (pro-anorexia), transgender hormone listservs, identity affirming social networking sites and interworked social movements. These groups with no say in cyberspace or cyberfeminism found ways to use it to affirm, rebel, and procure things for themselves.
Hall (1996) argues that there are two varieties of cyberfeminism. One variety draws from utopic elements of Haraway’s work on the cyborg and focuses on women's liberation through science and technology (Hall, 1996). The second variety is fueled by countering or eliminating male harassment in cyberspace (Hall, 1996). Both varieties use recurring themes that feminist scholars Rosa Braidotti (1996) and Susanna Paasonen (2011) identify as common strategic methods used in texts and artwork by cyberfeminist practitioners and scholars. These central themes are irony and parody/playfulness which are shown in cyberfeminist artwork, performances, text, and media.
Irony
Irony is a rhetorical trope that is often misunderstood. It shows “the contrast or incongruity between how things appear and how they are in reality” (Stanley, n.d, para. 4). Braidotti (1996) notes that the contradictory function of irony is how many cyberfeminists pull their humor. She notes that the combination of irony and (self) humor is shown in many cyberfeminist works. One sees this in OBN’s 1997 anti-theses. Instead of doing what has typically been done to define something, they did the opposite and created a list of things that run counter to how people may think about cyberfeminism. Paasonen (2011) adds that irony is “a cornerstone of cyberfeminism (p.343). While Solfrank (1998) sees the combination of irony, humor, and seriousness as “the quintessential cyberfeminist strategy, a productive tension that makes it possible to join contradictory views” (p.61). Cyberfeminists highlight the “inherent” contradiction of women not being involved in science and technology to get folks to understand the ridiculousness of the idea. Some cyberfeminists caution against using irony, especially when emphasizing diversity and inequality (Passonen, 2011; Solfrank, 2017). In cyberfeminist texts, irony has been used to create distance towards both “cyberculture” and “feminism” in ways that may obstruct, rather than facilitate, critical dialogue” (Passonen, 2011, p.344). For specific intersectional identities, like race and sexual identity, it may not be the appropriate strategy to facilitate change, it may not be ironic, it may be painful.
Parody/Playfulness
Art is the easiest way to see how the politics of parody and playfulness are utilized as a cyberfeminist strategy. Parody, like satire, involves social commentary on political issues, and as Faith Wilding stated, “the personal computer is the political computer,” so the use of parody and playfulness are geared toward making a political statement in cyberfeminism. To cyberfeminists, sex, and technology are also political. The visuals of VNS Matrix’s computer game All New Gen were described as “tongue-in-cheek” (Solfrank, 2017, para.13), and earlier, I described one of the promotional fliers for the First Cyberfeminist International as “cheeky.” As a cyberfeminist strategy, parody is typically associated with women’s sensuality and sexuality. The things that make women “weak,” like their sexual organs, are parodied as empowering. In All New Gen, the heroes do not use guns as weapons but slime from their clitorises. It is an intentionally crude detail that is playful, funny, and ironic. It serves as a reminder of the movement's goals, reducing gender disparities and liberating women through technology. It is seen through the “riot grrl” influence in early cyberfeminism from the zines, marketing materials, and other visual artifacts that constantly remind, tease, and emphasize women’s sexuality through technology. Braidotti (1996) analyzed a riot grrl text and wrote,
In other words, as a female feminist who has taken her distance from traditional femininity and has empowered new forms of subjectivity, the riot girl knows how to put to good use the politics of parody: she can impersonate femaleness in her extreme and extremely annoying fashion (p.8).
This in-your-face approach aims to capture attention by refashioning political issues people are familiar with but tinging them with consistently “cheeky” sexual humor. Braidotti (1996) adds that to use parody to be politically effective in cyberfeminism, it must be grounded.
Figure 5 shows an artistic contribution from VNS Matrix to the art book Cyberfeminism Index (Seu, 2023). This flier’s background image is of a giant clitoris with a space-like color scheme that features three mismatched half-dressed dolls, all of which are missing, obscured, and honed in vaginal areas. The accompanying text is “DNA SLUTS.” The text serves as a reminder that this image plays on the connotation of the word “sluts” by zoning in the dolls’ sexual organs. One would still need more context, especially if one did not find the image in the art book, but the image still grabs your attention and makes one think about the intent or point of this work. The importance of grounding your work when making parody or playful art emphasizing gender inequality should be framed as the central point when creating it. The point of making this kind of disruptive art must be grounded as it should be viewed as something that makes a point and inspires change, as Braidotti (1996) noted.

All in all, the term cyberfeminism may be dated, but its tenets, critiques, strategies, and themes can serve as interventions for contemporary issues of gender inequalities. These issues range from deepfake pornography, virtual sexual harassment, image-based sexual abuse, and more. Many unknowingly use cyberfeminist strategies and concepts. People utilize memes and gifs ironically and playfully to make political statements on social media. Others find community and belonging online based on their marginalized identities, while some subvert and challenge power structures through online and offline activism. In a world where the public is constantly reminded that women can be policed, ridiculed, and misrepresented simultaneously digitally and in real life, we may need a callback to cyberfeminism. This iteration of cyberfeminism must be grounded in diversity and inclusive of other marginalized groups like women of color and nonbinary folks because cyberfeminism can still be a way of liberation and countering misogyny, and it should start with those who remain at the bottom of the digital and real-world hierarchy.
Bibliography
Braidotti, R. (1996). Cyberfeminism with a difference. Futures of critical theory: Dreams of difference, pp. 239-259.
Cassell, J., & Jenkins, H. (Eds.). (2000). From Barbie® to Mortal Kombat: Gender and Computer Games. (MIT press).
Daniels, J. (2009). Rethinking Cyberfeminism(s): Race, Gender, and Embodiment. WSQ: Women’s Studies Quarterly, 37(1), 101–124. https://doi.org/10.1353/wsq.0.0158
Evans, C. L. (2014, December 11). An oral history of the first Cyberfeminists. https://www.vice.com/en/article/z4mqa8/an-oral-history-of-the-first-cyberfeminists-vns-matrix
Everett, A. (2004). On Cyberfeminism and Cyberwomanism: High-Tech Mediations of Feminism’s Discontents. Signs: Journal of Women in Culture and Society, 30(1), 1278-1286. DOI:10.1086/422235
Fernandez, M., Wilding, F., & Wright, M. (2002). Domain errors!: Cyberfeminist practices. (Brooklyn: Autonomedia).
Gajjala, R., & Oh, Y. J. (2012). Cyberfeminism 2.0. P. Lang.
Hall, K. (1996). Cyberfeminism. Pragmatics and Beyond New series, 147-172.
Haraway, D. J. (1985). Manifesto for cyborgs: science, technology, and socialist feminism in the 1980s. Socialist Review, no. 80. pp. 65–108.
Harlow, M.J. (2013). Cyberfeminism. In Stange, M. Z., Oyster, C. K., & Sloan, J. E. (Eds), The multimedia encyclopedia of women in today's world. (Vol 1-4). Retrieved from SAGE Publications, Inc. https://doi.org/10.4135/9781452270388
Langill, C. (2009). Shifting Polarities: Interview with Nancy Paterson. [Interview] Daniel Langlois Foundation Collection, Montreal, Canada. https://www.fondation-langlois.org/html/e/page.php?NumPage=1965
Net Art Anthology. (n.d.). A cyberfeminist manifesto for the 21st Century. Rhizome. Retrieved February 29, 2023, from https://anthology.rhizome.org/a-cyber-feminist-manifesto-for-the-21st-century
Oksala, J. (1998). Cyberfeminists and women: Foucault's notion of identity. NORA: Nordic Journal of Women's Studies, 6(1), 39-47. https://doi.org/10.1080/08038749850167923
Paasonen, S. (2011). Revisiting cyberfeminism. COMMUNICATIONS-EUROPEAN JOURNAL OF COMMUNICATION RESEARCH, 36(3), 335-352. DOI:10.1515/comm.2011.017
Plant, S. (1997). Zeroes ones: Digital women the new technoculture (1st ed.). (New York: Doubleday).
Richard, G. T., & Gray, K. L. (2018). Gendered play, racialized reality: Black cyberfeminism, inclusive communities of practice, and the intersections of learning, socialization, and resilience in online gaming. Frontiers: A Journal of Women Studies, 39(1), 112-148.
Russell, L (2020). Glitch Feminism: A Manifesto. (New York: Verso Books).
Scott, I. (2016, October 13). A brief history of cyberfeminism. Artsy. https://www.artsy.net/article/artsy-editorial-how-the-cyberfeminists-worked-to-liberate-women-through-the-internet
Seu, M. (Ed). (2023). Cyberfeminism Index. (Inventory Press).
Sollfrank, C. (1998). Female Extension. In C. Sollfrank & Old Boys Network (Eds.), First cyberfeminist international (pp. 60 64). Hamburg: OBN.
Sollfrank, C. (2017). Revisiting the Future. Transmediale. https://archive.transmediale.de/de/content/revisiting-the-future
Stanley, H. (n.d.). Irony: Definition, types, and examples. Writer. Retrieved February 3, 2023, from https://writer.com/blog/irony/
subRosa. (2013, February 21). What is subRosa?. https://archive.ph/20130221173356/http://www.cyberfeminism.net/about.html
VNS Matrix. (n.d.-a). The Cyberfeminist Manifesto for the 21st Century. Retrieved March 18, 2022, from https://vnsmatrix.net/projects/the-cyberfeminist-manifesto-for-the-21st-century
VNS Matrix. (n.d-b.). All new gen. Retrieved March 18, 2022, from https://vnsmatrix.net/projects/all-new-gen
VNS Matrix. (n.d.-c). Billboard project. Retrieved from https://vnsmatrix.net/projects/billboard-project
Wilding, F. (1998). Where is feminism in cyberfeminism? https://www.ktpress.co.uk/pdf/vol2_npara_6_13_Wilding.pdf
Vanessa Nyarko (December 2023). “A Callback to Cyberfeminism(s).” Interfaces: Essays and Reviews on Computing and Culture Vol. 4, Charles Babbage Institute, University of Minnesota, 50-61.
About the author: Vanessa Nyarko is a doctoral candidate in Communication Studies at the University of Minnesota-Twin Cities. Her research interests are in emerging technologies, media history, tech policy, and the political economy of media. She specializes in studies of the metaverse, Virtual reality, and reproductions of racism and sexism in digital spaces.
In the present moment, there are numerous discussions and debates about the function and even the possibility of memorization in artificial neural networks, especially in large language models (Tirumala et. al., 2022). A model that has memorized content from its training data is particularly problematic, especially when these models are used for generative tasks. Desirable outputs from generative models are those that closely resemble but do not exactly match inputs. Corporations developing and releasing these new technologies may make themselves vulnerable to plagiarism or theft of intellectual property charges when an output image matches those found in training data. Exceptional performance on natural language processing benchmarks or highly accurate responses to questions from academic and industry tests and exams could be explained by the inclusion of these objects in the training data. “Leaked” private information is also a major concern for text generative models and evidence of such information would create similar liability issues (Carlini et. al., 2021). While deep learning models do not record strings of text or patches of images within the major architectural components—their weights, specialized layers, or attention heads—information from the network can be reconstructed that can reveal sources used as training inputs. This behavior is known as memorization. Memorization is frequently understood to signify a failure of information generalization. Deep neural networks are designed to recognize patterns, latent or explicit, and generalize from the representations of these patterns found within the network—this is why they are called models. Concerns about the leaking of private information are serious but are not the only issues connected with memorization in machine learning; memorization of training data is especially a problem for the testing and evaluation of models. Neural networks are not information storage and retrieval systems; their power and performance are the result of their exposure to many samples from which they learn to generalize. There are different theories of “information retention” in neural networks and the material history of the early implementations of machine learning provides evidence for the ongoing slipperiness of the concept of memory in machine learning.
The concept of memory was used in multiple distinct ways in machine learning discourse during the late 1950s and early 1960s. The interest in developing memory systems during that historical moment was tied up in the relays between three overlapping issues: the status of machine learning systems as brain models, and related, the issue of perception and memory as mutually implicated, and finally the belief that specialized learning machines would be faster than conventional computers. The machines that gave machine learning its name were originally developed as an alternative to general-purpose digital computers. These analog machines needed to sense and store information acquired from input data. The various memory mechanisms proposed during this era functioned like semi-permanent non-volatile storage for these learning machines. They were also the weights used to learn the criteria for classification of input data. They thus played something of a double role in these systems. If the weights were the “programming” for these self-organized systems, then they function as a record of that programming. Serving as both data and instructions, these weights enable what we now call inference on the learned model, which is to say the classification of previously unseen inputs. Memory was not only the persistence of information within the model; it was also used to refer to the nature of the representations stored as information within the weights. Like the contemporary concern with memorization, an exact memory of inputs would mean that the model would likely fail to generalize, which is to say that it was not learning.
In Frank Rosenblatt’s April 1957 funding proposal for the research project known as “Project PARA” (Perceiving and Recognizing Automaton) that would eventually result in the creation of the Mark I mechanical perceptron, Rosenblatt described his recently articulated perceptron rule as not just a method for determining decision boundaries between linearly separable data but also as a way of conceptualizing memory: “The system will employ a new theory of memory storage (the theory of statistical separability), which permits the recognition of complex patterns with an efficiency far greater than that attainable by existing computers” (Rosenblatt, 1957). As a brain model—this was the motivating research paradigm that Rosenblatt would make clear throughout his unfortunately short life—research into machine learning and the perceptron was concerned with using these simulated neural networks to understand more about perception and brain function. While visual perception dominated early research, this area could not be unlinked from a concern with understanding how visual inputs were stored and how memories of previously perceived patterns were compared with new stimuli.
The “Project PARA” proposal outlines Rosenblatt’s architecture. The system would be composed of three layers: the sensory or “S-System,” an association or “A-System,” and finally the response or “R-System.” This architecture was imagined as a mechanical device and Rosenblatt anticipated this material manifestation of his design in all three layers. The “S-System,” he wrote, should be imagined as “set of points in a TV raster, or as a set of photocells” and the “R-System” as “type-bars or signal lights” that might communicate output by “printing or displaying an output signal.” The “A-System” would be the heart, or rather brain, of the perceptron by passing input from the sensors to the response unit by operating on the inputs in combination with pre-determined threshold value. The output from the multiple A-units, Rosenblatt explained, “will vary with its history, and acts as a counter, or register for the memory-function of the system” (Rosenblatt, 1957). References to the material origins of machine learning are scattered throughout the terminology of this field. The weights that are learned from samples of training data are called weights because these were weighted connections between mechanical devices. The A-System provided the Perceptron’s “memory function,” but what it was “remembering” within these weights would be the subject of some debate.
There were a number of other early analog “learning machines” that confronted the same problems encountered by Rosenblatt. After being exposed to the Perceptron while working as a consultant in the U.S., Augusto Gamba, a physicist at the University of Genoa in Italy created his own device known as the PAPA (derived from the Italian rendering of Automatic Programmer and Analyzer of Probabilities). Like Rosenblatt’s Perceptron, the PAPA combined memory and the statistical method for determining decision-making criteria:
A set of photocells (A-units) receive the image of the pattern to be shown as filtered by a random mask on top of each photocell. According to whether the total amount of light is greater or smaller than the amount of light falling on a reference cell with an attenuator, the photocell will fire a “yes” or “no” answer into the “brain” part of the PAPA. The latter is simply a memory storing the “yes” and “no” frequencies of excitation of each A-unit for each class of patterns shown, together with a computing part that “multiplies” or “adds logarithms” in order to evaluate the probability that an unknown pattern belongs to a given class (Borsellino and Gamba, 1961).
Gamba’s PAPA borrows the name “A-unit” from Rosenblatt’s idiosyncratic nomenclature (one of the reasons the PAPA has become known as a “Gamba perceptron”) for the Perceptron’s second layer, its hidden layer, although in Gamba’s architecture, the device’s “memory” is not found in the association layer but in the final “brain” unit.
The relation between the machine’s accumulated weights to the input data was an open problem and several different theories were used to explain and interpret the meaning of these values. For some historians of machine learning, the simplified mathematical model of a neuron proposed by Warren S. McCulloch and Walter Pitts has been assumed to be the major inspiration and basis for many working on the first neural networks (McCulloch and Pitts, 1943). While these McCulloch-Pitts neurons (as they are called) were incredibly influential, it was another theorical account that yoked together a model of perception and memory that would influence the architecture of the most important early neural networks. This was the decidedly non-mathematical work of Donald O. Hebb, a Canadian psychologist. Hebb’s The Organization of Behavior, proposes a theory that seeks to reconcile what otherwise appeared as two distinct accounts of memory by answering the question of “How are we to provide for perceptual generalization and the stability of memory, in terms of what the neuron does and what happens at the synapse?” (Hebb, 1949). Perceptual generalization is the idea that people can learn to generalize from just a few examples of a wide range of objects. As Hebb puts it, “Man sees a square as a square, whatever its size, and in almost any setting” (Hebb, 1949). The stability of memory was rooted in evidence of a persistent connection or association between particular stimuli and a set of neurons. Hebb theorized a solution to this impasse with the idea of locating (in terms of neurons) independent patterns of excitation. This idea was of obvious utility to machine learning researchers wanting to develop techniques to recognize objects like letters no matter where they appeared, for example, shifted to the left or the right, when projected on a two-dimensional set of sensors called the “retina.”
In an article appearing in 1958, Rosenblatt examined one theory of perception and memory that suggested that “if one understood the code or ‘wiring diagram’ of the nervous system, one should, in principle, be able to discover exactly what an organism remembers by reconstructing the original sensory patterns from the ‘memory traces’ which they have left, much as we might develop a photographic negative, or translate the pattern of electrical charges in the ‘memory’ of a digital computer” (Rosenblatt, 1958). Instead of memorizing inputs, Rosenblatt explained, the Perceptron implemented Hebb’s theory of learning and separated learned patterns from their exact inputs. “The important feature of this approach,” Rosenblatt wrote, “is that there is never any simple mapping of the stimulus into memory, according to some code which would permit its later reconstruction” (Rosenblatt, 1958). In these relatively simple machines and simulated networks, the association units might record the history of inputs as a collective representation, but they could not reproduce individual memorized inputs. For Rosenblatt, this was a sign of the success of the Perceptron; it demonstrated the practicality of Hebb’s theory by implementing a memory system in the form of weights that could be used for distinguishing between classes of data without memorizing distinct inputs used to train the network. This was also Rosenblatt’s grounds for differentiating the Perceptron from mere pattern matching: techniques developed contemporaneously with the Perceptron implemented databases of templates and accomplished pattern matching by memorizing and matching input samples to entries in a database (Dobson 2023).
Research on analog memory units connected two of the major sites in the development of machine learning: Rosenblatt’s lab at Cornell University in Ithaca, New York and Stanford Research Institute at Stanford University in California (Stanford University would shortly divest itself of the laboratory, which would then become known as SRI International). While Rosenblatt’s Mark I Perceptron is the best known of the early machines of machine learning, SRI had developed its own series of devices, the MINOS and later the MINOS II. While SRI’s first projects implemented the Perceptron, researchers would later develop an alternative learning rule. SRI’s MINOS project was a platform for evaluating different sensing and preprocessing techniques. George Nagy, a Hungarian-born computer scientist, worked with Rosenblatt at Cornell while a graduate student in electrical engineering; memory devices for neural networks became the subject of his dissertation and related research. Nagy worked with others in Rosenblatt’s Cognitive Systems Research Program (CSRP) group to design and construct a second-generation device called the Tobermory.

The Tobermory took its name from a short story by Saki (H. H. Monroe) that featured a talking cat. As its name suggests, it would be a “phonoperceptron” and designed for audio input. Nagy’s dissertation, defended in 1962, was titled “Analogue Memory Mechanisms for Neural Nets” and examined different possible designs for analog memory devices. Some of the existing options examined by Nagy included more experimental electro-chemical devices such as electrolytic integrators and solions and novel but difficult to use at scale film-based photochromic devices using slide projectors. Nagy settled on what was known as the “magnetostrictive read-out integrator,” a device suggested by SRI’s Charles A. Rosen. This was the tape-wound magnetic core memory device employed by the MINOS II and initially designed by SRI staff member Harold S. Crafts (Brain et. al., 1962). It also had the advantage of sharing features with the core memory used in conventional digital computers. The labor-intensive production of these memory devices, as Daniela K. Rosner et. al. argue, is one of several important sites of “hidden, feminized work” involved in the creation of mid-century computing (Rosner et. al., 2018). Addressing his selection of a tape-wound device for the Tobermory, Nagy wrote: “The chief virtue of the electromechanical integrator consists of its inherent stability. The ‘weight’ of a given connection is represented by a mechanical displacement, hence it is not subject to variation due to ambient changes or fluctuations in power supply level” (Nagy, 1962). Many existing analog alternatives, as Nagy notes in his survey, were subject to rapid decay, error, and sometimes were difficult to reinitialize or to erase previously stored values.

Despite the ongoing research and development of analog learning machines with memory devices during this period, many researchers were simultaneously implementing neural networks as simulated machines on conventional digital computers. In their justification for building a learning machine, the SRI MINOS team explained what they saw as the deficiency of digital computers: “Their major function in the present line of research is to simulate the performance of machine concepts which might be mechanized in some form which would be efficient (smaller, faster cheaper, etc.). The general-purpose digital machine thus appears as a research tool rather than as a final device for pattern recognition” (Brain et. al., 1960). In these simulations, the weights were stored in regular core memory during training and evaluation and persisted in various offline storage systems. The simulation of learning machines was necessary at the beginning of machine learning while engineers worked to construct analog machines and find appropriate memory devices, but this paradigm stuck as digital computers increased in speed and became easier to program and use. The appeal quickly became apparent to researchers. In an article summarizing his research into analog memory devices, Nagy speculated that advancements in digital computers might soon render analog memory obsolete. “In principle,” he wrote, “any pattern recognition machine using weighted connections may be simulated on a binary machine of sufficiently large capacity” (Nagy, 1963a). Specialized hardware for machine learning, although now fully digital and instrumented with layers of software, returned in the late 1980s and early 1990s during the high-performance massively parallel computer boom. Today, costly clusters of high-density graphical processing units (GPUs) and tensor processing units (TPUs) are being deployed to train very large models although these also execute software simulated learning machines.
Early machine learning was primarily directed toward the discrimination and classification of visual data. These models worked with highly simplified representations of images. They were not trained to generate new images. Today’s deep learning models in computer vision and the extremely popular Transformer-based large language models are now routinely used in generative applications. The size of these models combined with these new uses (themselves a function of model size), has prompted a reconsideration of the memory issue. The assumption that patterns of activation generalize, as Hebb theorized in biological models, seems to be under pressure when applied to understanding the operation of artificial neural networks with billions or more parameters. There is strong evidence that large language models are memorizing examples from their training and that this behavior is more likely in large models (Carlini 2021). The retention of this information suggests that these patterns can be mapped. Research into the interpretability of deep learning models has discovered some of these patterns and demonstrated that sets of neurons can be edited to alter the model’s predictions (Meng et. al., 2022). This line of inquiry returns us to lingering important questions about the relation between learning and memory, the differences between generalization and memorization, and the location of memory in neural networks that were also present at the founding of the field of machine learning.
Bibliography
Borsellino, A., and A. Gamba (1961). “An Outline of a Mathematical Theory of PAPA,” Del Nuovo Cimento 20, no. 2, 221–231. https://doi.org/10.1007/BF02822644.
Brain, Alfred E., Harold S. Crafts, George E. Forsen, Donald J. Hall, and Jack W. Machanik (1962). “Graphical Data Processing Research Study and Experimental Investigation.” 40001-PM-60-91.91(600). Menlo Park, CA: Stanford Research Institute.
Carlini, Nicholas, Florian Tramer, Eric Wallace, Matthew Jagielski, Ariel Herbert-Voss, Katherine Lee, Adam Roberts, et al. (2021). “Extracting Training Data from Large Language Models.” In Proceedings of the 30th USENIX Security Symposium. 2633–2650.
Dobson, James E. (2023). The Birth of Computer Vision. University of Minnesota Press.
Hay, John C., Ben E. Lynch, David R. Smith (1960). “Mark I Perceptron Operators’ Manual (Project Para)” VG-1195-G-5. Cornell Aeronautical Laboratory.
Hebb, Donald O. (1949). The Organization of Behavior: A Neuropsychological Theory. John Wiley and Sons.
McCulloch, Warren S., and Walter Pitts (1943). “A Logical Calculus of the Ideas Immanent in Nervous Activity.” Bulletin of Mathematical Biophysics 5, 115–33.
Meng, Kevin, David Bau, Alex Andonian, and Yonatan Belinkov (2022). “Locating and Editing Factual Associations in GPT.” Advances in Neural Information Processing Systems, 35, 17359-17372.
Nagy, George (1962). “Analogue Memory Mechanisms for Neural Nets.” PhD diss. Cornell University.
Nagy, George (1963a). “A Survey of Analog Memory Devices.” IEEE Transactions on Electronic Computers EC-12, no. 4: 388–93. https://doi.org/10.1109/PGEC.1963.263470.
Nagy, George (1963b). “System and Circuit Designs for the Tobermory Perceptron,” Cognitive Research Program. Report No. 5. Ithaca, NY: Cornell University.
Rosenblatt, Frank (1962). “A Description of the Tobermory Perceptron.” Cognitive Research Program. Report No. 4. Collected Technical Papers, Vol. 2. Edited by Frank Rosenblatt. Ithaca, NY: Cornell University.
Rosenblatt, Frank (1957). “The Perceptron: A Perceiving and Recognizing Automaton (Project PARA).” Report 85-460-1. Cornell Aeronautical Laboratory.
Rosenblatt, Frank (1958). “The Perceptron: A Probabilistic Model for Information Storage and Organization in the Brain.” Psychological Review 65, no. 6: 386–408. https://doi.org/10.1037/h0042519.
Rosner, Daniela K., Samantha Shorey, Brock R. Craft, and Helen Remnick (2018). “Making Core Memory: Design Inquiry into Gendered Legacies of Engineering and Craftwork.” In Proceedings of the 2018 CHI Conference on Human Factors in Computing Systems (CHI '18). ACM. https://doi.org/10.1145/3173574.3174105.
Tirumala, Kushal, Aram Markosyan, Luke Zettlemoyer, and Armen Aghajanyan (2022). “Memorization without Overfitting: Analyzing the Training Dynamics of Large Language Models.” In Advances in Neural Information Processing Systems 35. Edited by S. Koyejo et. al. 38274-38290. Vancouver, Canada: Curran Associates.
James E. Dobson (June 2023). “Memorization and Memory Devices in Early Machine Learning.” Interfaces: Essays and Reviews on Computing and Culture Vol. 4, Charles Babbage Institute, University of Minnesota, 40-49.
About the author: James E. Dobson is assistant professor of English and creative writing and director of the Institute for Writing and Rhetoric at Dartmouth College. He is the author of Critical Digital Humanities: The Search for a Methodology (University of Illinois Press, 2019) and The Birth of Computer Vision (University of Minnesota Press, 2023).
Artificial Intelligence (AI) has been shown time and time again to be a remarkable engine for codifying and accelerating inequality. Popular news media is literally littered with examples of AI gone wrong. Mortgage software has been found to recommend better interest rates for white borrowers (Bartlett et al.). Criminal justice AIs are more likely to recommend denial of parole for people of color (Benjamin). And all manner of bias has been found in search engine results (Noble). In each of these cases, the desire to develop and sell transformative new technologies got in the way of making fair and equitable systems. As a result, many in AI are looking for a better way. In her 2016 Weapons of Math Destruction, Cathy O’Neil (2017) argued that the future of AI needed a better “moral imagination.” AI and technology developers need “to explicitly embed better values into our algorithms, creating Big Data models that follow our ethical lead.” Since then, “ethical AI” has become an explosive area of investment and development.
There has been a proliferation of initiatives in industry, nonprofit, academia, and occasionally government—all devoted to better AI. We cannot really say that we are short on moral imagination at this point. In fact, I would go as far as to say that we are confronted by a dizzying array of competing moral imaginations. Different approaches to AI’s moral future vie for attention, leaving technologists with an expansive menu of options. But like the items on any menu, not all are of equal nutritive (moral) value. There’s good reason to believe that much of so-called Ethical AI is little more than window dressing (Burt). It’s handwaving at a vision of fairness that comes second to innovation and profit. There’s also good reason to think that even the best of intentions will not lead to ethical outcomes. This last issue is the focus of this piece. Much has been written about Ethical AI that’s little more than marketing. I want to think about how new technology designed to address a clear and obvious ethical need often falls short. In so doing, I reflect on a few recent attempts to develop AI for better pain medicine.
The Pain Problem
On a scale of 1-10, how much pain do you feel right now? This simple question, asked millions of times a day throughout the world, is state-of-the-art in pain measurement. The Numeric Pain Rating Scale (NPRS) and its cousin, the Visual Analog Scale (VAS)—sketches of progressively sadder smiley faces—are the primary ways that doctors assess pain. NPRS and VAS are low tech solutions that assist with the practice of pain management. Importantly, they do not really measure pain in any meaningful sense of the word. Rather, they help patients assign numbers to daily experiences and those numbers guide treatment. If your shoulder used to hurt at level 6, but daily stretching makes it hurt at level 3, we know that physical therapy is working.
The International Association for the Study of Pain (IASP) defines pain as “An unpleasant sensory and emotional experience associated with, or resembling that associated with, actual or potential tissue damage.” According to the best scientific minds who study the topic, being in pain does not require you to have an underlying physical injury. Have you ever winced when you saw someone else touch a hot stove? This is one reason why “potential” is such an important word in the IASP’s definition. You are in pain when you touch a hot stove, and you are in pain when you see someone touch a hot stove. Similarly, the same injury (when there is one) doesn’t cause the same pain in every person. Think about athletes who finish a competition on a broken leg, and only realize it after crossing the finish line. There was no pain until the situation changed, and then there was incredible pain. All of this is why the IASP’s definition of pain comes with a critically important note: “A person’s report of an experience as pain should be respected.”
Unfortunately, despite this recommendation from the IASP and even though the NPRS and VAS scales are the gold standard approach to pain management, the inability to directly measure pain is a regular complaint among healthcare providers. In my conversations with pain management doctors, many have expressed a strong desire for actual pain measurement. An interventional anesthesiologist I spoke to expressed frustration that he didn’t “have a way of hooking someone up to a pain-o-meter” (Graham, 2015, 107). Likewise, an orthopedist complained that “one of the first things those concerned will admit [is] there’s no algometer, no dial on somebody’s forehead. As long as you can’t read it out, you have to rely on the patient’s report” (Graham, 2015, 121). This desire for objectivity combined with the common denigration of patient reports as “merely subjective,” creates a situation where bias often runs amok in pain medicine. Increasingly, AI is being offered as a possible solution for such systemic inequities. In the context of pain management specifically, AI developers are working on what they hope will be that missing “dial on the forehead.”
Trust and Bias
Unfortunately, doctors don’t always trust what patients say about their own pain. Part of this has to do with that drive for objectivity. Part of this has to do with how we’ve responded to the opioid epidemic in this country. And part of it has to do with bias. A 2016 survey of medical trainees found that 73% believed at least one false statement about race-based biological differences (Hoffman et al). Among the most striking statistics was the fact that 58% believed that Black skin is thicker than white skin. This false belief and others like it have been traced directly to inequalities in pain management. Physicians routinely underestimate patient pain across patient groups, but the racial differences are striking.
Doctors are twice as likely to underestimate Black pain (Staton et al). As a result, Black patients are less likely to receive pain medication, and when they do, they routinely receive lower quantities than white patients. As these disparities are increasingly recognized by the medical community, recommendations for improvement tend to center around a mix of implicit bias training and increased reliance on more “objective” diagnostic technologies. The American Association of Medical Colleges, for example, recommends that in addition to implicit bias training, clinical guidelines should “remove as much individual discretion as possible,” and researchers should “continue the search for objective measures of pain” (Sabin).
Despite AI’s history of bias, it is frequently justified on the basis of its mathematical objectivity. Combine that with increasing investments in Ethical AI, and it creates the perfect environment for algorithmic pain measurement. And so, the developers of the new algorithmic pain prediction (ALG-P) system hope it will both provide more objective pain measurement and lead to reduced clinical biases (Pierson et al). Working with a diverse population of osteoarthritis of knee patients, the researchers trained the ALG-P to try and match patient reports. That is, they took X-rays of knees and linked those X-rays to each patient’s NPRS score, and the ALG-P system learned to identify certain patterns in the images that would predict NPRS values. Next, the study team compared ALG-P estimates of pain severity with those of the preexisting industry standard clinical decision tool, Kellgren–Lawrence Grade (KLG). The KLG, which was developed and validated on a predominantly white British population in 1957, guides human evaluation X-rays for osteoarthritis of the knee. ALG-P was 61% more accurate in estimating patient pain than the KLG. Importantly, however, while the ALG-P reduces the frequency and magnitude of racial disparities, it does not eliminate them. So, if a Black patient had a true pain level of 8, a doctor using KLG might estimate the pain at level 6, and one using the ALG-P might estimate it at a 7.
At first glance, ALG-P lives up to some of the best recommendations for Ethical AI. One common recommendation for better AI is to ensure that training data is labeled by members of the communities who will be most affected by the system and its use. A pervasive problem in pain medicine is that physicians tend to believe their own estimates of patient pain over those from patient reports. By training ALG-P on labeling data from patient report, the developers artfully sidestep this issue. In an interview with the MIT Technology Review, one of the study authors, Ziad Obermeyer, highlighted this more just approach as central to the study (Hao). Ultimately, both the study itself and some of the related media coverage indicate a hope that the availability of these data might encourage self-reflection leading to reduced clinical biases. As the study points out, “cooperation between humans and algorithms was shown to improve clinical decision making in some settings.” The MIT Technology Review article is even more enthusiastic, suggesting that “AI could make health care fairer—by helping us believe what patients say.” However, living up to one principle of Ethical AI does not necessarily assure that a given AI leads to a more ethical world.
Now, I have a few significant concerns about ALG-P. First, if we think back to the IASP definition of pain, it’s not all that surprising that the AI only leads to a 61% improvement. ALG-P looks at knee X-rays, physical features, and has no access to the psychological state of patients. We’re already missing a huge component of what it means to be in pain if we’re not including the psychological dimension. Also, as a researcher with longstanding interests in pain medicine, I am getting a powerful sense of déjà vu here. Doctors suddenly “trusting” patients when a new technology comes along and “proves” those patients right is becoming an all-too-familiar narrative. Almost 20 years ago, the case du jour was fibromyalgia—a chronic widespread bodily pain condition believed to be caused by difficulties regulating certain nerve signals. Fibromyalgia disproportionately afflicts women, another group many doctors seem to have trouble believing. But twenty years ago, then-recent advances in neuroimaging (PET, fMRI) were able to identify differences in how some people’s brains process certain stimuli. With “objective” technological verifications, doctors started to “trust” their patients.
Now, for many, this version of “trust” does not sound much like genuine trust. If trust is only extended to some patients when what they say is verified through technological “objectivity,” then there is no actual trust at all. What’s more, the average cost of a PET scan in 2020 was just over $5,000 (Poslusny). Even if insurance is reimbursing theses costs, that is a pretty steep fee for “trusting” women in pain. It is not yet clear if ALG-P will be used broadly and if so, how much will it cost patients? But if it’s anything like other computational imaging techniques, it could be pretty expensive for a product that offers around a 61% improvement. This is all the more problematic, of course, given that following IASP guidance and believing Black patients would lead to substantially more improvement while having the benefit of being free.
All-in-all, I have some pretty serious reservations about the extent to which this is an ethical addition to the practice of pain medicine. Importantly, this does not mean I think it’s impossible to make Ethical AI. The case of ALG-P suggests that it takes a lot more than a recognized injustice and a desire to do good in the world to ensure that a new system actually leads to ethical outcomes. Doing so requires more than just new technologies. This is another way of saying that an AI just isn’t going to fix inequality. AIs might be useful as part of a comprehensive approach that includes technical solutions, targeted education, and appropriate regulation. One of the biggest risks of the tech fix is that it will be understood as a “fix.” Maybe ALG-P is a good idea as a stopgap for those patients who are in pain and undertreated right now. But the long-term work toward justice has to continue while band-aid technologies offer partial improvements today.

Beyond the ‘Ethical’ Tech Fix
Ultimately, ALG-P is a textbook example of Ethical AI in a clinical context. Ethical AI tends to embrace a bias toward action. The ethical vision is grounded in the presumption that companies will build things. Thus, governance solutions and interventional technologies alike are engineered to guide (rather than prevent) that action. For the most part, this kind of interventional Ethical AI focuses on technologically engineered solutions to algorithmic bias. For example, one of the canonical works of Ethical AI proposes the following definition of anti-classification in ethical AI:
d(x) = d(x') for all x, x' such that xu = x'u (Corbett-Davies and Goel)
In English, “anti-classification” is largely a matter of not including identifying characteristics (including ethnic data) in AI systems. Of course, as many in critical algorithm studies have pointed out, the complex effects of systemic racism can create surrogate data points for race, such as zip code, which blunt a narrower approach to anti-classification. Although ALG-P was not developed in a corporate context, its underlying logics are remarkably similar to what we see in those contexts. In recent years, IBM, Facebook, and Google have all deployed new computational libraries designed to detect bias or engineer fairness in their algorithms. (IBM; Gershgorn; Google). Technologically oriented solutionism is precisely what allows some areas of Ethical AI to offer an apparently ethical intervention that is still ultimately subordinated to the dominant market logics of the corporation. In much the same way, ALG-P is an act of Ethical AI. To be sure, it is not situated in a corporate context, but it ultimately offers a tech fix that subordinates emancipatory aims to long-dominant clinical logics.
I’m certainly not the first to suggest that technologists need to think just as much about if they should act and when they should act, not just how they should act. There’s a massive cross-sector precautionary literature out there devoted to these kinds of questions. Inspired by that kind of thinking, I close this essay by considering how Ethical AI in healthcare contexts might address precautionary concerns in the face of ongoing harm to marginalized populations. Specifically, I suggest that those who wish to offer technological solutions to health inequity should, at the very least, address the following questions.
- Is the proposed intervention likely to substantially address an unmet or under-met community need?
- Have members of the communities most likely to be affected by the intervention been substantively involved in project conceptualization, putative benefits, risk assessment, data curation, and training set labeling?
- Does the project team have a robust plan for evaluating unintended consequences during design, development, testing, and distribution?
- Does the project team have a robust plan for supporting long-term community-centered justice-oriented initiatives in this area?
If the answer is not a resounding “yes” to all of these questions, then precaution (as opposed to intervention) is almost certainly the way to go. However, in the context of a robust community-led approach to development, then it may be appropriate to work at developing temporary technological fixes. That last question, however, is key. One of the biggest risks of the tech fix is that it will be understood as a “fix.” If healthcare is to work at developing and deploying band-aid technologies offering partial improvements in care, then the long-term community-led work of social justice has to continue and eventually replace those temporary technological scaffolds.
Bibliography
Bartlett, Robert, et al. “Consumer-Lending Discrimination in the FinTech Era.” Journal of Financial Economics, vol. 143, no. 1, pp. 30–56. ScienceDirect, https://doi.org/10.1016/j.jfineco.2021.05.047.
Benjamin, Ruha. (2019). Race after Technology: Abolitionist Tools for the New Jim Code. Polity, https://www.politybooks.com/bookdetail?book_slug=race-after-technology-abolitionist-tools-for-the-new-jim-code--9781509526390.
Burt, Andrew. (2020). “Ethical Frameworks for AI Aren’t Enough.” Harvard Business Review, 9 Nov. hbr.org, https://hbr.org/2020/11/ethical-frameworks-for-ai-arent-enough.
Corbett-Davies, Sam, and Sharad Goel. (2018). The Measure and Mismeasure of Fairness: A Critical Review of Fair Machine Learning. arXiv:1808.00023, arXiv, \ arXiv.org, https://doi.org/10.48550/arXiv.1808.00023.
Gershgorn, Dave. (2018). “Facebook Says It Has a Tool to Detect Bias in Its Artificial Intelligence.” Quartz, 3 May , https://qz.com/1268520/facebook-says-it-has-a-tool-to-detect-bias-in-its-artificial-intelligence.
Google. What Is ML-Fairness-Gym? (2019). Google, 1 Apr. 2023. GitHub, https://github.com/google/ml-fairness-gym.
Graham, S. Scott. (2015). The Politics of Pain Medicine: A Rhetorical-Ontological Inquiry. University of Chicago Press. University of Chicago Press, https://press.uchicago.edu/ucp/books/book/chicago/P/bo20698040.html.
Hao, Karen. (2021). “AI Could Make Health Care Fairer—by Helping Us Believe What Patients Say.” MIT Technology Review, 22 Jan., https://www.technologyreview.com/2021/01/22/1016577/ai-fairer-healthcare-patient-outcomes/.
Hoffman, Kelly M., et al. (2016). “Racial Bias in Pain Assessment and Treatment Recommendations, and False Beliefs about Biological Differences between Blacks and Whites.” Proceedings of the National Academy of Sciences, vol. 113, no. 16, Apr. pp. 4296–301. Pnas.org (Atypon), https://doi.org/10.1073/pnas.1516047113.
IBM. AI Fairness 360. https://aif360.mybluemix.net/. Accessed 2 Apr. 2023.
Noble, Safiya Umoja. (2018). “Algorithms of Oppression.” Algorithms of Oppression, New York University Press.
O’neil, Cathy. (2017). Weapons of Math Destruction: How Big Data Increases Inequality and Threatens Democracy. Crown.
Pierson, Emma, et al. (2021). “An Algorithmic Approach to Reducing Unexplained Pain Disparities in Underserved Populations.” Nature Medicine, vol. 27, no. 1, 1, Jan., pp. 136–40. www.nature.com, https://doi.org/10.1038/s41591-020-01192-7.
Poslusny, Catherine. (2018). “How Much Should Your PET Scan Cost?” New Choice Health Blog, 31 July, https://www.newchoicehealth.com/pet-scan/cost.
Sabin, Janice A. (2020). “How We Fail Black Patients in Pain.” AAMC, 6 Jan., https://www.aamc.org/news-insights/how-we-fail-black-patients-pain.
Staton, Lisa J., et al. (2007). “When Race Matters: Disagreement in Pain Perception between Patients and Their Physicians in Primary Care.” Journal of the National Medical Association, vol. 99, no. 5, May 2007, pp. 532–38.
S. Scott Graham (May 2023). “The Dangers of Ethical AI in Healthcare.” Interfaces: Essays and Reviews on Computing and Culture Vol. 4, Charles Babbage Institute, University of Minnesota, 32-39.
About the author: S. Scott Graham, PhD, is Associate Professor in the Department of Rhetoric and Writing at the University of Texas at Austin. He has written extensively about communication in health science and policy. He is the author of The Politics of Pain Medicine (University of Chicago Press, 2015) and The Doctor and The Algorithm (Oxford University Press, 2022). His research has been reported on in The New York Times, US News & World Report, Science, Health Day, AI in Health Care, and Scientific Inquirer.
Utah is an unparalleled exemplar of how creating a global center of excellence in an emerging specialty of computer science and engineering is possible with government seed funding. It was a special moment when the Advanced Research Projects Agency’s Information Processing Techniques Office (ARPA, IPTO) awarded the University of Utah $5 million ($43 million in today’s dollars) over six years, 1966 to 1972, for a project entitled “Graphical Man-Machine Communication” to launch the field of computer graphics and create a leading center for research and education. Three years earlier IPTO funded “Mathematics and Computation,” or Project MAC at MIT, also for six years, 1963 to 1969 (initially $2 million/year, but this grew to over $3 million/year). Given MIT’s Whirlwind (a real-time precursor to SAGE) in 1951, launching Lincoln Lab in that same year, and MIT spinoff nonprofit MITRE Corporation, in Bedford, Massachusetts, in 1958, past, major Department of Defense support had helped make MIT a top computing center prior. As such, Project Mac extended core areas of research and made an excellent computer science program far stronger. What was impressive about Utah was IPTO provided a half dozen years of support, far less than half the funds that IPTO awarded to Project MAC, and extremely talented and creative people ran with it and created a center of excellence anew. The Kahlert School has embraced the words of one its most famed and early doctorates (1969), Turing Award winner Alan Kay, “The best way to predict the future is to invent it.”
Dave Evans, Ivan Sutherland, other faculty, and graduate students made it happen in Utah. It changed from a program to a department (1973) to a school (2000), and throughout, it has achieved amazing feats. What came through so strongly in hearing talks, panel discussions, and meeting and engaging in conversations with the pioneers over two days in Utah this March, is that the research and development extending from the University of Utah and its alumni, was and is a product of a quite special culture.

Through the great leadership of Kahlert School of Computing Director Mary Hall, and the tremendous faculty at the school, that core, special culture, with some newer elements and commitments added, thrives today. Utah is one of the leaders in computer science and remains unmatched in graphics within computer science. The Kahlert School of Computing also impacts the world with newer tracks, such as Data Science and Software Development, and possesses a strong commitment to diversity, equity, and inclusion. Joining Hall and Dean of Engineering Richard B. Brown in this commitment to excellence and inclusion, it was also a pleasure to meet Vice President of the Kahlert Foundation, Heather Kahlert. The foundation’s support to the school recently led to its naming to become the Kahlert School of Computing, and her family foundation has supported an important initiative on inclusivity within the school, entitled “Programming for All.” Also impactful, John and Marcia Price recently made a $50 million donation to the College of Engineering, and their lead gift made the new, $190 million, John and Marcia Price building possible. Opening soon, it will house the Kahlert School of Computing and allow for its rapid expansion of existing and new areas of computing education and research.

There actually were three events on 23-24 March 2023 held in unison—the full day 50th Anniversary of the Computer Science Department of the University of Utah; followed on the second day morning IEEE Milestone Dedication; and then the afternoon Graphics Symposium. The three were complementary, reinforcing and expanding on each other in highly constructive ways. Most of the time, the program focused on looking back, but importantly, it also looked forward. Contributing to both was a fantastic day one keynote by Telle Whitney, past, longtime CEO of the Anita Borg Institute. Whitney is also co-founder of the Grace Murray Hopper Celebration, as well as of the National Center for Women and Information Technology (NCWIT). Nobody has done more to advance women in computing than Telle Whitney and to carry on the early work of her fellow computer scientist and collaborator Anita Borg.
On day two, consultant and IEEE Milestone Coordinator Brian Berg awarded an IEEE Milestone to the University of Utah Kahlert School of Computing for the department/school’s pioneering work in graphics. Berg presented the award to the school’s Director, Mary Hall, and the Dean of Engineering, Richard B. Brown.
This prestigious IEEE Milestone Award is an elite designation in technology. In computing, developments such as Bletchley Park Code-breaking; the ENIAC; MIT’s Whirlwind Computer (real-time); Moore’s Law; UCLA, and the (ARPAnet)/Internet have been awarded IEEE Milestones (which includes a bronze plaque—on day two, a video of Hall and Brown’s unveiling of the Utah CS plaque was played). Outside of computing, IEEE Milestones include Samuel Morse and Alfred Vail’s “Demonstration of Practical Telegraphy” in 1838; “Thomas Alva Edison’s Menlo Park Laboratory” created in 1876; and “Reginald Fessenden Wireless Radio Broadcast” in 1906. In short, it is a major honor and a useful IEEE program commemorating and exploring the past. Brian Berg has added much to the IEEE Milestone program, for more than a dozen years leading many IEEE Milestone efforts in the history of computing, software, and networking for IEEE Region 6, the Western United States.

Hall organized and was Master of Ceremonies for the magnificent day one “50th Anniversary of Computer Science at the University of Utah” symposium. She kicked off the event with an informative historical overview, drawing on the David Evans Papers and other archival materials.
Odd Ducks and Grand Challenges
ARPA funding was a necessary but not in itself sufficient element to foster Utah leading the way with the computer graphics revolution. Even having two of the most brilliant pioneers in computer graphics—hiring David Evans in 1965 to start the CS program and attracting Ivan Sutherland away from Harvard to join Evans—was not enough. The final, and arguably the most important ingredient, was the environment and culture that Evans set starting with his arrival (leaving the faculty of Cal Berkeley) in the mid-1960s, and that Sutherland contributed to mightily as well with his arrival in 1968.
There were other standout faculty in the early years, including but not limited to William Viavant, who served from 1964 to 1987, and the late Elliott Organick, who contributed to operating systems research and education and related areas of computer science with his nineteen books—including one I have devoured again and again on Multics and its security design (security and privacy are two of my areas of historical and sociological research). Also contributing to first-day events were impactful faculty who joined the department in the 1980s and beyond. They added greatly to the event and showed the breadth of the department in so many areas of computer science—Al Davis, Duane Call, Chuck Seitz, and Rajeev Balasubramonian. Program alum, Kahlert School Research Professor, and Flux Research Team Co-Director Robert Ricci’s moderation of a panel with graduates David Andersen of Carnegie Mellon and Cody Cutler from Amazon was especially intriguing in exploring “…Network Research, from ARPANET to Emulab and Beyond.”
Alan Kay is among the first and most famed of Utah CS doctoral alums (1969). His quote on inventing the future is fitting given he helped build the office of the future at Xerox PARC in the 1970s. Kay provided leadership in creating windows-oriented graphical user interfaces (GUI) and made major contributions to object-oriented programming (OOP), including his pivotal leadership creating the OOP-optimized Smalltalk language with Adele Goldberg, Dan Ingalls, and others. Kay’s presentation was by video, and focused on Dave Evans, Ivan Sutherland, and the environment of CS at Utah in the 1960s. Another, early and long-famed graduate, Jim Clark, also invented the future in founding Silicon Graphics and later Netscape. He, too, gave a brief and inspired talk on day one—his was in person.
As a social and organizational historian of computing, Utah has long fascinated me, and I have enjoyed the oral histories that have been conducted by past and current colleagues of the organization I am now privileged to direct, The Charles Babbage Institute for Computing, Information, and Culture. Perusing our unparalleled archives on computer graphics (many collections), and reading and re-reading the secondary literature has been a joy—including and especially past CBI Tomash Fellow Jacob Gaboury’s stellar, award-winning new book, Image Objects: An Archeology of Computer Graphics, and long ago, Founding CBI Director Arthur Norberg and Judy O’Neill’s classic Transforming Computer Technology: Information Processing for the Pentagon, 1962-1986.
How does an ARPA grant and two extremely gifted scientists create an unparalleled global center of excellence at a state school with a smaller state population (about 30th)? How does it succeed in fostering such an organizational culture to attract and cultivate the people to succeed on such a grand scale? Beyond Evan and Sutherland’s leadership gifts, high standards, and generosity, I would argue that not being surrounded by an overall, existing elite (Ivy or equivalent like MIT or Stanford) institution was a major plus. It helped facilitate the freedom for the faculty and students to experiment, to take risks, and to think big. That was my belief before traveling to Utah for the two days of events, and it was reinforced by the program, reminiscences, and discussions there.
Evans and Sutherland’s entrepreneurial drive shaped the department and pioneering graphics company Evans and Sutherland, but it was not the Silicon Valley style entrepreneurism of moving fast and breaking things. Instead, it was tending to the necessary money and resources side of the equation, and focusing on the nurturing and creative sides, more akin to a metaphor raised at the event several times, to “cultivating a garden.” This was a garden that encouraged talented graduate students, faculty, and company team members to grow the next new thing, the code, the tools, and the devices that could have a positive impact on science, knowledge, work, and leisure. Over the two days of meetings, the importance of the physical setting came through as a meaningful factor as well, the mountains and their tremendous beauty, the skiing, the retreats, and the frequent computer science meetings held at the picturesque Alta Lodge.
In starting a new program and seeking a certain culture that was different from other emerging schools in computer science, Evans looked for outliers in the graduate students he (and colleagues) admitted to the program. The seeking of “odd ducks,” was foundational and essential to the intellectual freethinking, and creative culture that he cultivated with the program from his formation of it in 1965 (the Computer Center launched in 1958 and grew to a staff of 30 people), one of 11 such programs at the time.
In 1968, with Ivan Sutherland’s arrival, resigning from his Associate Professorship in Computer Science at Harvard to become a Professor of Computer Science at Utah, and the ARPA IPTO funds, the program really took off. He and Evans were the two top researchers in the new field of graphics—they essentially invented it. Sutherland especially so, with his path-breaking 1963 dissertation on Sketchpad. Sketchpad was a legendary computer graphics program that transformed computer science. It influenced so much—from Human-Computer Interaction (HCI), Computer-Aided Design (CAD), object-oriented programming to GUIs, and virtual reality (VR). He had the additional insight to do a film demo that conveyed to the emerging field of computer science that a new major domain within it, graphics, was possible.
As Sutherland reflected during a panel at the event, ARPA IPTO Director J.C.R. Licklider had convened a group of top scientists and military leaders to see Sketchpad and meet with him. Despite his young age Sutherland was essentially a legend shortly after his dissertation. In 1964, Sutherland, only twenty-six years old, followed Founding Director Licklider in taking the reins to become the second ARPA IPTO Director, funding basic research largely at universities that helped transform the new field of computer science in areas such as time-sharing, AI, and other early graphics and networking work. Two of the most important grants in IPTO’s history were Project Mac (by Licklider in 1963) to MIT in artificial intelligence and time-sharing (Multics) and the six-year grant (by Robert Taylor in 1966) to the University of Utah in graphics. Other critical 1960s IPTO grants provided the basis of the ARPAnet. Utah has the distinction of being one of the four nodes of the ARPAnet at its launch as a four-node network in 1969.
Given Evans’ and Sutherland’s immediate respect for each other, their visionary, and entrepreneurial personalities, they became immediate friends and collaborators. And coming together at Utah was also about starting a company. Sutherland reminisced with a smile, whether Evans was to join him in Cambridge, or he was to go to Utah came down to “he [Evans] had seven kids and I just two.” It was fortuitous for both scholars, for the field of graphics, for the U, as Utah is affectionately known. It was also beneficial to the company, Evans and Sutherland. The University of Utah likely had greater opportunity for freedom than Sutherland’s Harvard, Cambridge, or Boston might have had for the company. Evans and Sutherland cultivated an overlapping family-type environment in both settings and endeavors. For the company, this made it all the easier to retain its talented computer scientists over the long term—good people tend to job-hop more in Silicon Valley and in Boston/Cambridge.
Evans and Sutherland, trailblazing graphics commercially, increasingly brought the technology to the world in a fast-growing range of applications. They attracted a top venture capital firm in Hambrecht and Quist, and their company was soon valued at $50 million. In just ten years, it grew from $10 million in revenue to $100 million in revenue.
As Sutherland conveyed about himself and Evans, and many others at the recent symposia reinforced, at the University of Utah Computer Science Department and at Evans and Sutherland, the two leaders sought to have as flat organizations as possible. Also important to them was assuring the satisfaction of everyone contributing to something larger than themselves. Seeking and solving hard problems was key to the student and employee/researcher’s satisfaction. The challenges could add to a sense of common purpose and a closeness of individuals and feeling part of the team. The graduate students became part of Evans’ and Sutherland’s extended family and they frequently had them to their homes to socialize.

Early Graphics
The many images shown at the event exemplified the words of the largely retired set of standout graduates who spoke and participated in its panels. This included showing a costume party photograph of playful attire and big smiles on the faces of faculty and graduate students in the Evans’ home. Regarding the company, Evans and Sutherland, there is one data point that goes beyond just the speakers and hints at the broader experience of employees being very positive and a family-like atmosphere, it is the retirement group and its continuing so many years. This sizeable group has a picnic reunion each year, the large numbers of people coming to this event year after year is suggestive of the positive culture of the company over decades.
Is there a potential risk of exaggeration or embellishment of the culture given the people speaking at the event had impressive careers and legendary accomplishments—a selection bias? Certainly, and further research into this culture through oral history, the David Evans Papers, and other archives likely would be fruitful and fascinating. For now, it seemed to me the group was large enough, and the message clear enough from people speaking, often quite emotionally, and always in a way uniquely their own, to get a telling sense of this culture and environment that Sutherland and Evans, the people, and Evans and Sutherland the company, created.
The participants in the event (especially the second day symposium specifically on graphics) were primarily graduate students from the late 1960s and the 1970s (though not exclusively). In the images and the talks there were tremendous accomplishments of alumni from multiple continents. Nonetheless, most were white and male. This was not unique to Utah. Diversity of gender participation and inclusion were challenges across computer science prior to a mid-1980s peak in women majors (reaching 38 percent), as well as from the early 1990s forward to today. Women’s participation as CS majors has generally been in the teens to low twenties, and at times the lower teens, apart from the mid to late 1980s. As such, Telle Whitney’s wonderful talk on gender, both historical and prescriptive, and highlighting some incredible women, added so much to the event.
For the remainder of this essay reflection, I will discuss several keynotes and other talks that especially resonated for me regarding University of Utah Computer Science Department/School of Computing culture and carrying of this culture impactfully into the broader world by faculty and alumni. In selecting a handful to discuss, I want to stress that all of the panel discussions and talks were compelling and fascinating, and many I do not highlight in what follows also exemplified the special culture of CS and The Kahlert School of Computing at the University of Utah.
Impacting the World at Scale: Nvidia, GPUs, and LLMs
Steve Parker gave a compelling keynote address on “Utah and the Frontiers of Computing.” Like a number of doctorates of the program, he later was a professor within it. For the past sixteen years he has been at Nvidia, and he currently serves as Vice President, Professional Graphics at the corporation, which has strategically led in skating to (and inventing and shaping) where the puck is going, rather than where it has been (such as Intel did in stumbling fashion), in microcircuitry—leading the way with Graphical Processing Units. GPUs are central to gaming, an area Nvidia has long served, and the far larger opportunity is that they are now also concentrating on large language models, machine learning, and many application areas. As OpenAI, Microsoft, and Google are seeking to exploit the opportunity for general markets and consumers (in my mind with too little HCI and user experience research and testing of how ChatGPT and Bard might amplify societal biases and extend inequalities, as search has done), Nvidia is focused on enterprise and targeting verticals.
In addition to some wonderful graphics displays Parker and his team did for the presentation, he refreshingly acknowledged the ethical critique with "search" and the importance of research and ethics in getting things right to have a positive impact on the world with large language models, with applications of generative artificial intelligence. A theme throughout was how researchers and leaders at corporations such as himself are “standing on the shoulders of giants” in Evans, Sutherland, and others. This is very much true in both the technical sense and organizational and decision-making sense with stewardship of machine learning out in the world. Parker concluded on a humorous note, with a slide of song lyrics after he asked ChatGPT to “Write a rap song on the history of computer graphics at the University of Utah.” To give a brief sense…. Verse 2 (1980s) … “In the eighties, Pixar joined the crew; and they worked on RenderMan, which was something new. It made computer graphics look oh so fine; And it’s still used today, it stood the test of time…”
Gender, Inclusion, and Innovations of Extraordinary Women
While ethics was a portion of Parker’s talk, it was the focus Telle Whitney’s excellent keynote address which preceded it on day one. Whitney was an undergraduate at the University of Utah and went through several potential majors before settling on Computer Science (BS 1978). These included Theater, Political Science, and English. She took an Interest Inventory Test and scored exceedingly high in programming. An advocate for her was Professor Richard F. Riesenfeld. Whitney earned her Ph.D. from Caltech in Computer Science working under the legendary Carver Mead, the co-inventor of Very Large-Scale Integration (VLSI), with Xerox PARC’s Lynn Conway. Doctorate in hand, by the mid-1980s she went on to technical and managerial positions at semiconductor companies Actel and Malleable Technologies. She also held senior leadership roles at a few tech startups. With her friend, Anita Borg, she was co-founder of Institute for Women and Technology, which Borg ran until she became terminally ill with brain cancer. In 2002 Whitney, initially temporarily, took over to lead the institute as CEO, which was renamed as the Anita Borg Institute, and later AnitaB.org. She ended up staying and was the CEO and President until she retired from role in 2017. In 1994, Borg and Whitney launched the Grace Hopper Celebration, which that year was a gathering of 500 women, an event for research, socializing (including dance parties), recruiting, and professional support. It has continued to grow steadily and is tremendously impactful to those who attend and to advancing women’s access and opportunities in computer science. There is a long way to go, but AnitaB.org, the Grace Hopper Celebration, and NCWIT are powerful and positive forces.

Whitney spoke about the Anita Borg Institute and its co-founding of the Grace Hopper Celebration that started strong and has only grown since. Participation rates of women in computer science remains a challenge. In the biological sciences there is near gender parity (around 50 percent) women. In computer science, in recent years, numbers have been around 20 percent women at the bachelor’s and at the Doctoral degree levels, while a bit higher for Master’s, but still under one-third. Women’s participation in computer science even lags that of engineering overall. The early part of Whitney’s address was on underrepresentation of women historically and today and the very important point that it is both an inequity and to the detriment of computer science, losing out on so much talent and creativity.
The last two-thirds of Whitney’s talk was profiling five women and what they are doing in leadership, advocacy, and as role models to advance issues of equity and inclusion for women in computer science. Whitney offered rich cases of all five, I provide brief mention below.
- Cecilia Rodriguez Aragon—Professor of Human Centered Design and Engineering at the University of Washington, who co-invented treap data structure.
- Ashley Mae Conard—Computational biologist who works as a Senior Research at Microsoft Research.
- Aicha Evans—Computer engineer who served as Intel’s Chief Strategy Officer. In 2019 she became CEO of Zoox, a self-driving technology firm, and remains CEO of the Division after Amazon acquired Zoox for $1.3 billion.
- Mary Lou Jepsen—CEO of Openwater and co-founder of One Laptop per Child.
- Fei Fei Li—Professor of Computer Science at Stanford who in 2017 started AI4All and Co-Director of the Stanford Institute for Human-Centered Artificial Intelligence.
Whitney began studying CS at Utah, became a standout computer scientist and entrepreneur in industry, and has been an unparalleled leader for women in technology in leading AnitaB.org for fifteen years. Her message is important for all higher education institutions, one insightfully and inspirationally conveyed through biographical cases of these five tremendously accomplished and impactful women.
Utah and Influencing Corporate Cultures—Evans and Sutherland and Far Beyond
Dave Evans and Ivan Sutherland, by all accounts of the people on the program and in the audience, created an atypical corporate culture at their company that was analogous to how they built the University of Utah’s program/department into a center of excellence. This included seeking driven individuals who were creative and interested in tackling and solving big problems. It also included a non-hierarchical management structure with few layers. This was evident in Robert Schumaker’s insightful and engaging presentation. He joined General Electric (GE) in 1960 working on visual simulation systems but ran into dead ends in trying to get customers to contract for his and Rodney Rougelot’s work on flight simulators. Without the contractors signing on, GE was not supportive of continuing the work. The two were recruited away by Evans and Sutherland in 1972 and had the freedom and the runway to succeed, and they did mightily for the company. While photos of basic one-story buildings and trailers Schumaker showed of Evans and Sutherland's "campus" may not have been impressive or inviting compared to GE, the environment and support was. Schumaker and Rougelot led work that resulted in selling 1,000 flight simulators to various airlines globally a mere year after joining the more conducive team atmosphere of Evans and Sutherland. Schumaker became Simulation Division President and after two dozen years with the company, Rougelot rose to become President and CEO of Evans and Sutherland in 1994.
The culture that Evans and Sutherland built (at the university and the company) shaped how founders and leaders managed at some of the most influential graphics and software companies in the world. This included at Pixar Animation Studios and Adobe.
Ed Catmull gave one of the most moving talks of the event. It began with his account of his graduate student days. In the doctoral program in its early years, he had classes with Jim Clark, Alan Kay, and John Warnock. Catmull made major advances in computer graphics contour and textual mapping. He went on to do pioneering work in film graphics but ran into difficulty selling the ideas and his early work, that is until Lucasfilm hired him in 1979 and he became Vice President of the Computer Division of Lucasfilm. In 1986 Steve Jobs acquired this division of Lucasfilm, which became Pixar.
Catmull is a co-founder of Pixar Animation Studios and worked very closely with Jobs. He was emotional in emphasizing writers have the early Steve Jobs, in his first stint at Apple Computer, pegged appropriately (his impatient difficult personality and disrespect of others) but fail to recognize that the experience of being pushed out of Apple changed Jobs. He expressed how the Jobs he worked with in leading Pixar was a changed man (it is not uncommon for journalists writing history to prioritize the story they want to tell, a sort of truthiness over truth). At Pixar, both prior to and after it was taken over by Disney in 2006, there was a culture of commitment to completing projects and taking the time and putting in the resources to do them right. Catmull articulated how Pixar and Disney had parallel functional departments and units, sometimes benefiting from each other, but had their own culture and identity. This was key to success, and it runs counter to ideas in management with M&A, of integration and eliminating overlap and laying people off to capitalize on efficiency. Catmull stated another key lesson (one taken from Utah) is participation in decision-making and processes and keeping powerful people out of the room or reducing the number of them in the room. These were keys to Pixar’s success with Toy Story (with the Utah Teacup a part of it of course); Toy Story II, III, and IV; Finding Nemo; Ratatouille; and its many other creative achievements and blockbuster hits.
Sutherland Still Future-Focused in His Stellar Presentation
At various times Ivan Sutherland took the stage on panels, and offered remembrances, interesting anecdotes, perspectives, and historical details. It was his end of the day one keynote that stood out for me. He gave a technical and overview talk on Single Flux Quantum as a wholly new path for the greatest challenges in computing today.
As Sutherland related, the challenges today to extend Moore’s Law, inability to continue to add/double components on a chip, or it drastically decelerating, amounts to hitting a “power wall.” This is what is limiting computing’s future as he sees it. Sutherland gave a powerful and compelling talk advocating for Single Flux Quantum as a path to pursue to address this challenge. It is distinct from both the Moore’s Law methods and paradigm as well as from quantum computing. The latter may be a few decades out still and will work for some scientific and engineering purposes, but far from all or even most applications in computing. In Single Flux Quantum, magnetic flux is quantized. Sutherland stated the worst part of semiconductors today are the wires. Single Flux Quantum does not have this problem, further it is fast, digital, and Turing complete. It has some challenges and Sutherland went through each, arguing the payoff could be tremendous and if the US does not do it other nations will.

To do Single Flux Quantum right, Sutherland advocated for government funding for 1,000 engineers to work on it. He emphasized Utah should be a part of this. In his twenties, in the 1960s, with Sketchpad and Head Mounted Display, Sutherland invented computer graphics, VR, Object-Oriented Programming, and more. Also, in his twenties (mid-twenties at that) he led ARPA’s IPTO in skillfully funneling funds to worthy projects that would change computing. At Utah he and David Evans, and their company, were soon beneficiaries of their own IPTO funding, and they did change the world. The impact of their students and former employees is profound and continues. I, like 99 percent plus of the population, do not have the technical understanding to assess Single Flux Quantum , but the case Sutherland made for it seemed deeply researched and informed. More importantly, some of the fraction of one percent who understand it were in the room. The questions after it, from top engineers, were also strong and some quite challenging. Sutherland handled them masterfully. At age 84 Sutherland is doing what he has always done, and it is line with a famed quote of one of his early star students Alan Kay, “the best way to predict the future is to invent it.” While Sutherland, by his own acknowledgement, will not likely lead the effort to conclusion given his age, he is seeking to be a policy advocate for it in a highly informed way and doing this in his typical virtuoso fashion. It was moving and resulted in an extended standing ovation from all.
Bibliography
[Most of this reflection/review essay is drawn from the presentations at the three events described over the two days put on by the Kahlert School of Computing at the University of Utah, 23-24 March 2023. Below are some books, articles, oral histories, and archives collections that have influenced my thinking on the history of computer graphics.]
Alias Wavefront Records. Charles Babbage Institute for Computing, Information and Culture Archives. University of Minnesota.
“COE Receives Major Gift.” (2023). COE Receives Major Gift, New Name - The John and Marcia Price College of Engineering at the University of Utah (January 11, 2023).
Gaboury, Jacob. (2021). Image Objects: An Archeology of Computer Graphics. (MIT Press).
Machover, Carl Papers. Charles Babbage Institute for Computing, Information and Culture Archives. University of Minnesota.
Misa, Thomas J. (2010). Gender Codes: Why Women Are Leaving Computing. (Wiley-IEEE Press, 2010).
Norberg, Arthur L. and Judy O’Neill. Transforming Computer Technology: Information Processing for the Pentagon, 1962-1986. (Johns Hopkins University Press, 1996).
Smith, Alvy Ray. (2010). A Biography of the Pixel. (MIT Press).
SIGGRAPH Conference Papers. Charles Babbage Institute for Computing, Information and Culture Archives. University of Minnesota.
Sutherland, Ivan Oral History, conducted by William Aspray, 1 May 1989, Pittsburgh, Pennsylvania. Charles Babbage Institute, University of Minnesota. Oral History Interview with Ivan Sutherland (umn.edu)
Jeffrey R. Yost (April 2023). “From a Teapot to Toy Story, and Beyond: A Reflection on Utah, Computer Science, and Culture.” Interfaces: Essays and Reviews on Computing and Culture Vol. 4, Charles Babbage Institute, University of Minnesota, 19-31.
About the author: Jeffrey R. Yost is CBI Director and HSTM Research Professor. He is Co-Editor of Studies in Computing and Culture book series with Johns Hopkins U. Press, is PI of the new CBI NSF grant "Mining a Usable Past: Perspectives," Paradoxes and Possibilities in Security and Privacy. He is author of Making IT Work: A History of the Computer Services Industry (MIT Press), as well as seven other books, dozens of articles, and has led or co-led ten sponsored projects, for NSF, Sloan, DOE, ACM, IBM etc., and conducted/published hundreds of oral histories. He serves on committees for NAE, ACM, and on two journal editorial boards.
In 1965 Gordon Moore observed how semiconductors evolved over time in both how they increased their capacity to hold and process data and how their costs declined in an almost predictable manner. Known as Moore’s Law, over time it proved remarkably accurate. This essay suggests that his observation could lead to a clearer definition of a Moore’s Law type of consumer behavior. Unlike in Moore’s case, where its proponent had observed close-up the evolution of computer chips and one could use his insight to generalize, we have less empirical evidence with which to base a precise description for how a consumer behaves.
Hence, doing the same with respect to consumers is more difficult. That is our reality. I hypothesize that consumers of digital technologies behaved as if they were knowingly applying Moore’s Law to their acquisition, use, and replacement of digital goods and services. The paucity of evidence about their behavior is evidence that we do not know how much one can generalize the way Moore did. One’s own experience with computing devices suggests the notion has possibilities.
People, living in the nation where this law first became evident in continuous innovations of microprocessors, became some of the earliest users of consumer digital electronics, from watches in the 1970s to PCs in the 1980s, the Internet and flip phones in the 1990s, to smartphones and digital home assistants in the 2000s. As use of digital products increases, the need to understand how consumers decided to embrace such technologies becomes urgent beyond business circles to include academic study of the role of information in modern society.
This essay suggests that at least one lesson about digital innovations understood by historians may be useful in assisting business leaders, economists, public officials, and other historians to understand why individuals became extensive users of digital products. It draws from Moore’s Law as a rough gauge of how hardware performance and costs evolved applied to users’ experiences.
This essay discusses how scholars could study consumer behavior. It is a call for users of all manner of computing-based technologies to be studied by testing the hypothesis that consumers may have behaved in a Moore’s Law sort of way. Because computing historians are already familiar with the role of Moore’s Law on the supply side of the equation, they should be able to use that tacit insight to begin understanding the demand side of the story.

Photo credit: IntelFreePress, https://www.flickr.com/photos/intelfreepress/8575080587/sizes/o/in/photostream/
The Historian’s Problem
Historians face the problem of understanding how and why people adopted so many digital consumer products in essentially one long generation. Digital consumer products account for over 50 percent of all IT sales in the world, the other half are traditional company-to-company sales. Sales are annually in the trillions of dollars and continue to increase at rates faster than do national economies. Sales of consumer electronics increased between 4 and 7 percent annually over the past several decades, as less “advanced” economies expanded their consumption of such devices too, notably, in recent years, in China and India. This constitutes an annual market of $1.7 trillion, not including costs of using Internet services, just devices and software. So, studying early adoption of PCs by students, or writing on the history of computing companies of the 1950s-1980s, is insufficient.
In one sense, this is an old conversation about the diffusion of technology. Economists and historians feel they understand the issue, because they rely on neo-classic economic theory to explain what is happening by studying how people pick what to appropriate based on their best interests. In such thinking, neo-classical economics is based on the assumption that people know about a particular technology and use such knowledge in their purchasing decisions. Consumers exhibit rational behavior. Such thinking also acknowledges that people pay a price for acquiring whatever information they have with which to make a decision. That sense of full rationality is being questioned by behavioral economic thinking. In 2017 economist Richard H. Thaler was awarded the Nobel Prize in Economics for demonstrating that people can act irrationally too, also that this behavior can be predicted. His work encouraged economists to identify how consumers behaved that way. If the underlying idea of Moore’s Law reflects consumer behavior, then economists and historians have a way of viewing how users of digital technologies approached them.
Between the 1960s and the end of the 1980s, business historians and others who focused on the evolution and adoption of technologies proffered an alternative explanation, called path dependency, to explain that current decisions were—are—strongly influenced by prior decisions. This prism made sense for decades, as scholars in multiple disciplines grappled with this latest general-purpose technology called computing. The problem is that none of these types of explanations are substantive enough to lead to more robust insights as to why and how individuals embraced IT so quickly, given that most consumers did not have sufficient technical insights that neo-classical economic thinking assumes. Path dependency, or perhaps lock-in, inches closer in assisting, but only in explaining why one device might seem more attractive than another once they are already familiar with a particular type of equipment, software, or process. If one were replacing their Apple smartphone with another Apple smartphone, path dependence explanations are helpful. But such thinking does not explain why that same individual acquired an Apple phone in the first place.
Historians have nibbled at the problem. Familiar examples include Ruth Schwartz Cowan, Trevor J. Pinch, Nelly Oudshoorn, and Frank Trocco, all who looked at how to study consumer behavior through a sociological lens. In 1987, Cowan recommended focusing on a “potential consumer of an artifact and imagining that consumer as a person embedded in a network of social relations that limits and controls the technological choices that she or he is capable of making.” Pinch and his collaborators advocated for case studies to identify relationships of technologies, relevant social groups, and consumption choices applying sociological methods. However, as Cowan observed, these scholars “have given us a prescription but precious few suggestions about how it may be filled.” So, the problem introduced in this paper has been with us for a long time yet to be resolved. Perhaps using Moore’s Law can provide a more prescriptive approach, furthering Cowan’s thinking and of social constructionist-oriented historians.
Table 1 is a list of some of the most widely adopted digital consumer products. While incomplete, it suggests the necessity to appreciate the diversity of devices, even before any conversation about myriad versions of each that appeared simultaneously and incrementally by thousands of vendors. IT experts avoided forecasting a slowdown in the evolution of general-purpose computing. As the sale of older technologies slowed, because so many people already had them (e.g., smartphones, laptops), new ones attracted them, such as intelligent home speakers, virtual reality products, and wearables.

Introductory Dates for Major Digital Consumer Products in the US* | Year |
|---|---|
| Microwave ovens | 1967 |
| Digital watches | 1972 |
| Handheld calculators | 1972 |
| Cellular telephones | 1973 |
| VCRs and videos | 1975 |
| Desktop computers (PCs) | 1975 |
| CD players | 1982 |
| Portable consumer telephones | 1983 |
| Betamax movie camera | 1983 |
| IBM PC and clones | 1981-1984 |
| Battery operated laptop computers | 1988 |
| Game consoles | 1980s |
| Digital home movie cameras | 1991 |
| Internet access | 1993-94 |
Digital cameras
| 1994 |
Flat TV screens
| 1997-99 |
| DVD players | 2003 |
| Blu-Ray players | 2006 |
| Smartphones | 2007 |
| Programmable home thermostats | 2008-2010 |
| Tablets | 2010 |
| Digital personal assistants | 2011 |
Smart (video) doorbells
| 2012 |
*Dates reflect when consumers at large were able to acquire these products.
How Economists Explain Demand for Consumer Electronics
Traditional economic thinking holds that consumer technologies are “public goods,” things widely available to anyone who desire them. To become available to “anyone,” requires that the consumer understand its value, has means to acquire, and is willing to pay for these. Most will not pay $5,000 for a Dell computer today but would for one at less than $500. Technological knowledge is also an important factor.
There is growing interest in the role of technical knowledge that makes these devices more accessible to consumers. Increasingly, people know that IT goods—hardware—are used with software to transform other goods, making them more valuable, such as computing to improve fuel efficiency in a car. Consumers see that as an advantage worth investing in for their car. In the 1980s, economists like Paul Romer added that injecting growing bodies of knowledge into goods made these of greater value. This is the idea of applying knowledge about a technology embedded in the actions of consumers, not just in the minds of those inventing new products. How else could one rationalize acquiring a PC in 1982 for $3,000 or an Apple phone in 2018 for $999? Economists argued that the abundance of knowledge created more value than scarcity. Debates around those issues continue, but as one observer explained, “It is the growth of knowledge that is the engine of economic growth,” and that means all manner of knowledge use, including what consumers thought. Economists explain that someone interested in acquiring a long-established product could find a great deal of information to inform their purchase decision, but less for new products just coming onto the market.
Consumers acquired IT products because they provided a utility or fulfilled a desire. PC users wanted to consume digital content (i.e., read the news, view a movie, or play a game), or to produce it, for instance word processing, or to send email. One question economic historians should want to explore is to what extent was that behavior attributable to general-purpose technologies evident with respect to digital tools and toys?
A new breed known as behavioral economists is examining the psychology of economic behavior. Some of these have concluded that, “economic value,” (i.e., price) still dominates purchase decisions trumping, but not eliminating, the power of emotional or social attractions. Experimentation with such phenomenon as the attraction of ring tones suggests people do not buy digital products just to improve their productivity, challenging older neo-classical economic beliefs. Often consumers acquired these for enjoyment, such as flat screens or online games, again value being consumption. Music, in particular, stimulated considerable demand for IT in the post 2000 period, while a decade earlier, video games. To appeal (entertain), social values of a particular technology and their playfulness had a role. Entertainment and social interactions provided the most significant motivator to acquire digital products.
Economists argue that consumers will not always have perfect knowledge of a digital product, so make mistakes, that is to say, do not always make the best choices to optimize their economic advantage. Consequently, consumers learn to avoid these. But, digital products are used so individualistically that users rely on personal experience to characterize benefits of a product (the idea that my use of an Apple PC is different than yours). The more effective they are in tailoring use of a digital product to their needs the more one can assume their attraction to it increases, even if the journey to that satisfaction is bumpy or long.
Knowledge of the product (genre of products and technologies) combined with experience with these is highly influential and normal. But like traditional economists predict, consumers learn what they want, balance needs and desires against costs, then act rationally. That line of reasoning remains economic orthodoxy and scholars in other disciplines have yet to see strong reason to challenge it. Historians seem more interested in how people value a digital product than economists who are more concerned with prices, each focuses on different issues.
Anthropologists began exploring the role of individuals in their acquisition of personal computing. Their earliest studies were based on consumer behavior of the 1980s and early 1990s. For example, in a study of the experience of English families acquiring PCs, they were treated as miniature institutions (e.g., like a company). They acquired the least expensive machines available, but then more frequently additional hardware and peripherals. Their acquisitions spilled over into other electronics with nearly half acquiring additional televisions and cassette players, some more tape players. As the study observed: “purchase of one or more home computers has also been stimulus to further purchase of more traditional brown goods.” Husbands had twice as much experience with PCs (presumably from job activities) as women and led the charge to acquire digital products. Once knowledge of a new class of products diffused into their homes, adaption escalated quickly. Neighbors and work colleagues had clearly talked to each other, at least among professional and managerial classes. So, points go to the economists because of affordability issues, while familiarity with the technology and its features shaped responses of households to these products. Influencing acquisition in both a Moore’s like fashion and path dependency, games played on television in the 1980s moved quickly to PCs.
What Marketing Experts Say About Consumer Behavior with Digital Products
Marketing professionals focus on how consumers react to such offerings. They have much to teach scholars in other disciplines. They want to predict how consumers will respond to new products and to persuade them to buy new ones. They argue that a consumer’s existing knowledge asserts major influences on their decision to acquire a digital product. The more knowledgeable a consumer is, the more likely they are to benefit from its use. Someone with knowledge of one technology is less likely to move to a novel one requiring new insights than a novice not wedded to an earlier digital device or software. If you are used to Microsoft Word on a Lenovo laptop, you are willing to accept new releases (editions) of either more readily than, say, to try a new word processing software operating within Apple’s operating system.
What can we learn about early adopters, individuals who appropriate a new digital product before the public at large? Marketing experts obsess over them because they are crucial to the success of a new product’s acceptance by consumers. Economists and historians pay insufficient attention to them. Early adopters often represent 10 percent of a new technology’s supporters and it is their successful use of a new product that encourages others to acquire these. “Influencers,” as they are called, tell relatives and friends how great (or terrible) a new product is and offer advice on how to deal with these. Peer influence plays an important role. College students are famous for being early adopters of smartphones, video games and tablets, and since they are physically near where marketing professors work, they represent a convenient, if not ideal, cohort for gaining insights. The more friends one had encouraging a specific purchase (or use), the more likely a student would adopt the device or new use (i.e. an app). Family influences play a statistically significant role in adoption decisions, too.
Just as semiconductor firms felt compelled to conform to Moore’s Law, so to consumers came to depend on and expect consumer goods manufacturers to introduce products that reflected productivity improvements expected of the semiconductor firms. These expectations suggest that consumers intertwined with that of semiconductor firms, creating a hidden interdependence between them and their suppliers, hence with marketing, because the latter had to document such behavior and then encourage it.
Role of Speed and Churn in Technology Options
General technologies emerged and diffused faster the closer one moved toward the present: a new automobile is today designed and produced in 24 to 36 months, as opposed to 48 months in the 1980s. It took over a half-century for telephones to be installed in over 50 percent of American homes, but only a decade for mobile phones. The list of examples is extensive. Older technologies took longer to diffuse to substantial levels, such as electricity, telephones, and radios, quicker for television. Rates of diffusion of digital products sped up in comparison. The number of innovations increased, as did both the speed with which they appeared and with which people acquired them. Our interest here is on the adoption rates of technologies.
Everett Rogers in his classic studies on the diffusion of innovations identified early adopters as crucial in explaining its uses and benefits to slower adopters who shared common interests. They tended to be younger, better educated, more affluent, informed, extrovert, and willing to take greater risks that their use of a new device would malfunction or fail exceeded what their neighbors or colleagues were prepared to embrace.
| Device | Years to 75% Adoption | Years to Estimated 25% Adoption |
|---|---|---|
| Microwave oven | 15 years (1967-1992) | unknown |
| Digital watch | unknown | 1970s |
| PC | 24 years (1978-2002) | 16 years |
| Portable phone | 25 years (1978-2003) | 13 years |
| VCR | 5 years (1988-19930 | 5 Years |
| Internet | 23 years (1993-2015) | 7 years |
| Digital camera | unknown (1986) | late-1990s |
| Smartphone | 10 years (2007-2017) | 3 years |
| Flat screens | unknown | unknown |
*Dates and percentages are estimates based on multiple chronologies and statistical data compiled using different data and calculating methods. Source: Census Bureau, US Department of Commerce.
Table 2 lists a sampling of digital devices and how long it took for 25 percent, then 75 percent, of the American public to acquire them. Implicit with these products was appropriation of the software necessary to operate them. The public took less time to acquire digital devices as they went through one decade after another. There is some debate about how to measure these rates of adoption, as the data in table 3 suggests. However incontrovertible is that the rate of acceptance sped up over decades worldwide, with only rates of diffusion differing from one nation to another.
| Device | Years to 50% Adoption by Home |
|---|---|
| PCs | 19 years |
| Cell phones | 14 years |
| VCRs | 12 years |
| CD players | 11 years |
| Internet access | 10 years |
| Digital TVs | 10 years |
| DVD players | 7 years |
| MP3 players | 6 years |
*Source: Adapted from US government sources by Adam Thierer, “On Measuring Technology Diffusion Rates,” Technology Liberation Front, May 28, 2009, https://techliberation.com/2009/05/28/on-measuring-technology-diffusion-rates/ (accessed July 2, 2012).
This trend is made more impressive because each category of products underwent significant technical and usability changes, causing users to learn new ways of doing things, an attribute of new products that normally should delay embracing a new generation of their devices. This happened, for example, when either Microsoft or Apple announced it would no longer support an earlier operating system, forcing users to change software, often also hardware. Smartphone manufacturers attempt to force the same behavior but have been most successful when adding functions, such as cameras.
To sum what is understood so far: Users worried about the complexity of a new device or service compared to their prior experiences. They were influenced by prior experiences, expectations, and relevance of specific goods to them. Peers, family, and reviewers influenced their views about a digital offering. They compared incremental changes of one device or software to another and how these fit into their path-dependent knowledge of a technology. Increasingly over time, they became concerned about the effects of an adoption on the privacy of their information.

A Proposed Explanation for When Individuals Embrace Technologies
My proposed explanation can be stated as a question because the hard evidence required to answer it in the affirmative is currently spotty, while the logic is attractive: Have users of digital technologies subconsciously learned to behave according to a variation of Moore’s Law?
Moore’s Law is partially enigmatic because it evolved over time. By the mid-1970s he was saying that changes in capacity and lowering of costs came every 18 months. That meant the cost of a transistor (its capacity) would decline at a predictable rate, helping to explain how computers became less expensive and smaller over time. Moore pointed out that his observation was not an expression of a phenomenon in physics or natural law, but rather, of an historical trend. That is an important distinction because his was a statement of how technologists could choose to behave; it was an expectation. Intel, which he ran, chose to develop new generations of semiconductors that doubled in capacity every 18 to 24 months for decades. Sufficient knowledge existed to implement such choices.
Can Moore’s observation be used to understand how people outside of a semiconductor factory responded to the innovations that came from within the computer industry? This question implies that regardless of the law’s future relevance, it asks if its prior manifestation is the right question useful to guide research about consumer behavior. One would expect that an engineer, computer scientist or vendor’s employee conscious of the law would integrate that insight into their personal behavior. That individual could be expected to delay by a year or two their acquisition of, say, a flat-screen confident that the $5,000 initial asking price would drop by some 20 percent compounded per year. But it is not clear that most people had such explicit insider knowledge of Moore’s Law, or even knew someone who did. Given the speed with which every new class of digital devices was appropriated by the public suggests that neither of these few “technically-in-the-know” few million individuals, including early adopters, were not enough to sway the behavior of hundreds of millions of users.
Let us restate the key hypothesis that should be studied: Consumers time their acquisitions consistent with the rate of innovations and pricing explained by Moore’s Law. It is as if consumers knew Moore’s Law and applied it to optimize when and what they acquired. Consumers know when to buy because of their prior experiences with digital devices, all of which reflected Moore’s Law at work. And how do we know that they have that prior experience? The well-documented sales data collected by vendors and governments preserve it, as do the three tables in this essay.
A corollary is that consumers subconsciously accepted that their behavior and use of digital devices transferred from one to another. Hand-held remote controllers, first acquired for TVs in the 1970s, are used today for turning on and off gas fireplaces, indoor lights, computational devices, and garage doors. Smartphones are routinely used as remote controllers for managing programmable devices in the home; key fobs to lock and unlock automobiles. Examples abound once one realizes that functions can be transferred from one device to another. Vendors encouraged that sense of universality. Apple conspicuously promoted integration of its products for decades, that is to say, their ability to communicate with one another, aiding lock-in to the Apple ecosystem. This ecosystem includes app store infrastructure, third-party platforms, and other cloud infrastructure—third-party social networking, of course, is economically viable because of the Moore’s Law trajectory and monetization of data in advertising. It also requires common user interfaces and ways of using devices from one to another. Apple sees that universality of function as a competitive advantage over Android devices. Consumers call for digital devices to communicate with their other digital goods, much as IT professionals demanded of IBM and its competitors for their workplaces since the 1960s.
Embedded in this corollary is sufficient confidence required to make acquisition decisions involving digital products, including new ones. Buying one’s first or second PC required significant research and courage, not just a great deal of money; far less so one’s first laptop. Then, or as a few years earlier (i.e., 1970s), moving from a desktop electronic calculator to a hand-held H-P digital calculator had the same effect. When the old H-P died, acquiring its replacement was hardly a conscious decision, it happened quickly. It helped that the consumer knew that before buying the replacement it would be far less expensive than the original H-P, unless H-P had added functions to newer models. People knew what any calculator could do and more-or-less how to use them. This same representative consumer took less time to decide to acquire a digital camera than their original 35-mm film one, and in the process enjoyed a bargain and far more functionality, even if the base camera cost the same as their original film camera. When flip phones first appeared, which consumers viewed as another advanced electronics product, with digital photography already part of their experience with other digital products, again the decision came quicker, and even faster with smartphones a half decade later, which included digital photography. Consumers became increasingly confident that they knew what they were doing, that risks of mistakes diminished in buying decisions, and that costs were manageable. In each instance, expectations were subconsciously set and met.
Underlying all this behavior was a growing body of experience, of tacit knowledge about digital consumer goods acquired over decades. A new generation of economists, psychologists, and marketing experts recognized the power of knowledge tied to social values and attractions in influencing decisions. While they still segmented users into such groups as experts, early adopters and laggards, users behaved essentially the same way. Acceptance had to “fit” prior experience and perceptions.
How Could Moore’s Law Be Leveraged Through Historical Perspective?
One can envision the hypothesis—research agenda—as a test to explore several issues. First, an attitude to embrace originates from taking the perspective of the consumer. Second, there have been so many consumer electronics introduced in the past half-century for which case studies are needed, almost on an item-by-item basis, such as about those in Table 1, to understand how each was acquired and used. Increasing our understanding of specific experiences with each test whether people were influenced by their prior experiences with others. That requires case studies.
As case studies are prepared, what kind of Moore’s Law-centric questions might one ask? Some of the most obvious include for each device or software the following:
- In what order did a consumer or group of consumers acquire new electronic devices and software? This is a question of chronology to establish the order of decision-making.
- Why was the new device acquired? Was it a new version or software release or an entirely new class of products (e.g., tablets, not a flip phone)? This gets to the issue of path dependency, because historians know that it occurs at the individual level, not just in corporate or governmental decision-making, yet we do not know if it crosses product lines.
- What role did prior experience with digital devices have on the decision to acquire a new, or different class of products? Following from Moore’s Law should chip manufacturers’ learning of how to improve on earlier components through experience also apply to consumers? The answer is not certain, but important to study further.
- What effect did a consumer’s interaction with other users (not just advertising, marketing, and good sales personnel) have on their acquisition and subsequent experience with their acquisition? The hypothesis here is that social or professional networking is a critical element, a deep bow to pioneering scholars Cowan, Pinch, and others.
- Does a user’s familiarity with a specific type of digital product lead that individual to choose a higher price device? Is that applied knowledge or simply comfort, or are the two ideas one and the same?
- What role does platform tribalism play? Is this like bikers reinforcing each other to always ride a specific brand of motorcycles? Is such conformance limited to specific cohorts and age groups, such as teenagers who are notoriously famous for being loyal to what is fashionable at the moment?
Outputs of such research can be framed in language familiar to those who study Moore’s Law. For one, measuring the time it takes to make an acquisition compared to when a device became available is a crucial source of evidence in support of the hypothesis that Moore’s Law behavior may be in play. Did the amount of time from when digital cameras became available in one national economy to when 25 or 50 percent of its population had one shorten as compared to the earlier acquisition of PCs? Did adoption of smartphones after digital cameras shorten even further, or not, as a result that prior experience with digital photography? If so, why? The assumption that the behavior is broad has to be tested, too. How fast should be measured and compared against how quickly smartphones with cameras were acquired?
Differentiate subclasses of users by individual needs and existence of specific digital goods. Early adopters behaved differently than naive consumers in each period. Active resistors did too. We do not know if initial appropriations are reflections of Moore’s Law behavior, or if more the case after a consumer has stepped onto the treadmill of a particular technology, which this essay suggests possibly reflects Moore’s Law once commenced and more certainly path dependency. My assumption is that a correlation exists, probably too, as a cause for the decline in film-based camera sales. But it has to be proven and reasons for that behavior verified. Another assumption that consumers understand they can port over specific functions from one class of products to another, confident in their ability to do so and to achieve the same results, needs validation.
Economists who looked at Moore’s Law are right to focus on relationships between innovations and costs to those who purchased the results. The same can be applied to consumer behavior. At a country level, but then at an industry level too, we need statistics cataloging the number of digital items acquired by consumers by year, device, then in comparative tables, so that one can do the necessary analysis to determine quantitatively rates of adoption. Similar data gathering followed by analysis of changing costs to consumers should be done to determine effects pricing had on rates of adoption. Built into the Moore’s Law hypothesis is the assumption that as goods dropped in price, more were sold and that after a while users came to expect a certain rate of price/performance changes to occur. Did that, in fact, happen? If not, the hypothesis weakens. If the correlation followed by validating consumer testimony is established, then the hypothesis is strengthened.
Economic Implications of a Consumer Moore’s Law
With so much spent on consumer digital electronics and other devices that share functional and economic characteristics, marketing, psychologists, and economists are studying how buyers and users behave. Do consumers, for example, approach acquisition and use of such technologies differently than non-digital goods? The answer is partially, but increasingly, yes, because they have to invest more time and energy to learn about a new device and how to use it, thus once understood are going to use that knowledge as criteria to judge future acquisitions. A vendor cannot introduce a product without training and considering its compatibility with prior devices and hope for the best. If they did not, people might be expected to continue to use 20-year-old releases of Microsoft Word or that ancient digital watch received as a Christmas present in 1975, rather than a smartwatch.
Second, products previously not thought as fitting under the umbrella of digital products are moving into that space. Tesla automobiles are seen as digital products manufactured by a Silicon Valley management team. What effect did the dearth of information have on consumer behavior, as was the case with information regarding health care options in the United States in the 1990s, or as the British recently experienced with Brexit? Already, consumers of medical services are trying to “play the odds” on when a cure, say, for their cancer will appear, hence shape their interim strategy for treating their condition. Home medical monitoring devices or wearables are rapidly coming onto the market, welcomed by these same consumers who earlier acquired smartphones, digital cameras, PCs, and the oldest, microwave ovens, VCRs and watches.
Third, consumers are learning about the nuances of using all manner of digitized products and services that affect their views. There is a body of studies about consumers transporting expectations from one industry to another, even to mundane activities with no apparent involvement of computing on their minds. It is easy to imagine them taking lessons learned in non-digital parts of their lives and applying them to digital products and conversely back to our concern, porting insights from one technology or knowledge base to another. Historians can increase our understanding of massive sets of activities involving billions of people.
A concern that the hypothesis makes obvious is If people anticipate and act upon price declines doesn’t Moore’s Law then reflect how it influences supply-side behavior? We do not know the answer with respect to consumers. If the answer is yes, that consumer behavior is more influential on the demand side, then is/was Moore’s Law less influential on users? What needs to be determined is whether consumers were just reacting to Moore’s Law for producers. Our hypothesis assumes the answer is not so clear; there is an agency at work on both sides of the supply/demand paradigm.
Implications for the History of Information Technology
Historians have studied the supply-side of consumer electronics more than about users of such devices and software. Yet, consumers massively outnumbered suppliers and employers. For example, Apple had 132,000 employees, but 588 million users of its products in 2016, more of both in subsequent years. Similar observations can be made about other digital products. As use of digital goods continues to seep into every corner of life and society, historians of most disciplines will encounter these and need to deal with their behaviors. This is a daunting task, because users of computing are fragmented cohorts. It is easier to write a history of IBM, for example, than about IBM’s customers; I know, because I tried. However, the concept of consumers acting as if applying Moore’s Law can be a helpful meme assisting scholars to deal with the effects of the digital.
Economist Kenneth J. Arrow was an early student of how asymmetric information affected behavior, arguing that sellers had more facts about a product than consumers. His insight stimulated decades of discussion about the role of information in economic activity, although the conversation had started in the 1950s. Further exploration of the notion of a consumer Moore’s Law might alter that information balance-of-power, tipping it more to the consumer, reinforcing another line of Arrow’s research that held there existed a general equilibrium in the market in which the amount of supply of something matched demand for it, more or less. He argued that consumer behavior involved “learning-by-doing,” which, as concept and observation, are compatible with the new psychological economics. His notion is also consistent with a Moore’s Law behavior by consumers, if we semantically modify it to “learning-by-using.” Enough research has been done on how consumers respond to digital products to confirm that learning becomes a core element affecting adoption of digital goods.
One could, of course, take the position that consumers are simply conforming to an old behavior that they replace technologies as new ones come along. That argument would only apply to a replacement, say, of an older release of Microsoft Word with a newer one, but not if a consumer in the 2000s added tablets and smartphones to their tool kit, or started using wearables. One could posit the null hypothesis that consumers respond to digital electronics the same way they do to other products. That requires no critique, because the reader knows that is not true; furniture, and pots are not the same as digital goods—these require little economic risk or investment of time when compared to electronics. Digital products operate with their own rates of innovation and production of new classes of goods and services, which is why we need to search for methods with which to understand them. That is why a lesson from the Moore’s Law experience might prove insightful.
Bibliography
Arrow, Kenneth J. (1984), Collected Papers of Kenneth J. Arrow, vol. 4, The Economics of Information, Belknap Press, Cambridge, Mass.
Brock, David (2006), Understanding Moore’s Law: Four Decades of Innovation, Chemical Heritage Foundation, Philadelphia, Penn.
Cowan, Ruth Schwarz (1997), A Social History of American Technology, Oxford University Press, New York.
Pinch, Trevor J. and Frank Trocco (2002), Analog Days: The Invention and Impact of the Moog Synthesizer, Harvard University Press, Cambridge, Mass.
Rogers, Everett M. (2005), Diffusion of Innovations, Free Press, New York.
Thaler, Richard H. (2016), Misbehaving: The Making of Behavioral Economics, W.W. Norton, New York.
James W. Cortada (March 2023). “Can Moore’s Law Teach Us How Users Decide When to Acquire Digital Devices?” Interfaces: Essays and Reviews on Computing and Culture Vol. 4, Charles Babbage Institute, University of Minnesota, 1-18.
About the author: James W. Cortada is a Senior Research Fellow at the Charles Babbage Institute, University of Minnesota—Twin Cities. He conducts research on the history of information and computing in business. He is the author of IBM: The Rise and Fall and Reinvention of a Global Icon (MIT Press, 2019). He is currently conducting research on the role of information ecosystems and infrastructures.